The SafePay ransomware group has shortly grow to be a strong operator since its preliminary detection in September 2024, marking a startling enhance within the cyber menace state of affairs.
Not like predominant ransomware-as-a-service (RaaS) fashions that depend on associates for dissemination and profit-sharing, SafePay operates autonomously, with its core builders immediately orchestrating intrusions and extortion campaigns.
This self-contained method has enabled the group to assert duty for over 265 victims globally by early 2025, marking a pointy enhance from simply over 20 targets in 2024.
Self-Operated Ransomware Risk
The group’s double-extortion technique includes not solely encrypting victims’ information with strong algorithms but in addition exfiltrating delicate knowledge for leverage, threatening publication on a devoted Darkish Internet leak web site (DLS) if cryptocurrency ransoms stay unpaid.
SafePay’s aggressive ways have disrupted operations throughout numerous sectors, underscoring the evolving sophistication of non-affiliate ransomware operations that prioritize precision and evasion over widespread affiliate-driven proliferation.
Rising nearly undetected till its sudden surge, SafePay has leveraged a modular ransomware binary configurable through command-line parameters, permitting tailor-made encryption of particular drives whereas incorporating self-deletion mechanisms post-execution.
The malware embeds geofencing checks that terminate operations on techniques utilizing languages comparable to Armenian, Azerbaijani (Cyrillic), Belarusian, Georgian, Kazakh, Russian, or Ukrainian, successfully sparing Commonwealth of Unbiased States (CIS) areas a standard indicator of menace actors avoiding jurisdictions with potential affiliations or prosecutorial dangers.
This selective concentrating on aligns with SafePay’s deal with developed economies, the place high-value payouts are extra possible, additional evidenced by their avoidance of CIS-aligned domains and infrastructures.
Targets, Strategies, and Defensive Methods
SafePay’s victimology reveals a pronounced emphasis on North America and Western Europe, with the US bearing the brunt at 103 confirmed incidents comprising practically 40% of circumstances adopted by Germany with 47.
Further strikes span the UK, Australia, Canada, and choose Latin American and Asian nations, predominantly affecting manufacturing, expertise, schooling, enterprise companies, and healthcare sectors, alongside transportation, finance, agriculture, and public companies.
This broad industrial concentrating on exploits organizations prone to operational downtime, the place the stress to revive entry typically outweighs the dangers of non-payment.
Operationally, SafePay adheres to a refined cyber kill chain, initiating entry by means of stolen credentials procured from Darkish Internet markets or infostealer campaigns, typically bypassing multi-factor authentication (MFA) through misconfigured firewalls or phishing/vishing hybrids involving real-time social engineering over platforms like Microsoft Groups.
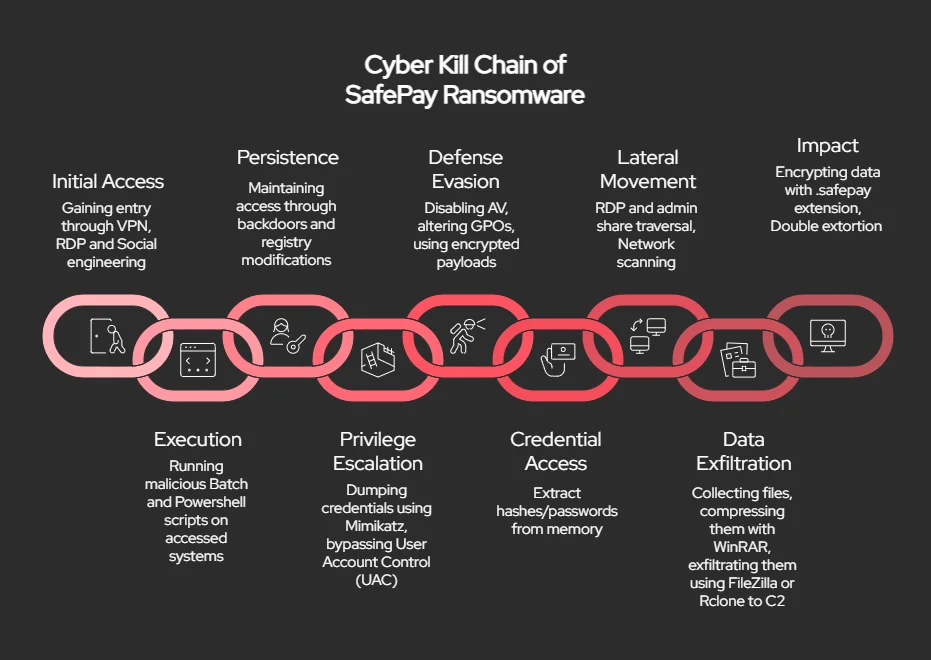
Put up-breach, execution leverages living-off-the-land binaries (LotL) comparable to regsvr32 and cmd.exe for code injection into reliable processes, whereas persistence is achieved through instruments like ConnectWise ScreenConnect or customized backdoors like QDoor, obfuscated for anti-analysis.
Privilege escalation exploits instruments like Mimikatz for credential dumping and consumer account management (UAC) bypasses, enabling protection evasion by means of antivirus disablement, Group Coverage manipulations, and deletion of occasion logs and quantity shadow copies.
Lateral motion makes use of RDP and administrative shares, with knowledge exfiltration performed through FileZilla or Rclone to siphon gigabytes of compressed archives.
Based on the report, the influence culminates in file encryption appending the .safepay extension, accompanied by readme_safepay.txt notes directing victims to TON-hosted portals for negotiations.

Mitigation in opposition to SafePay calls for a multifaceted defense-in-depth posture, emphasizing fortified entry controls with enforced MFA, distinctive passwords, and common account audits to thwart preliminary credential abuse.
System hardening by means of well timed patching of VPNs, RDP endpoints, and uncovered companies, coupled with endpoint detection and response (EDR) monitoring for anomalous behaviors like LSASS entry or uncommon PowerShell invocations, can disrupt execution and lateral phases.
Limiting abusable utilities, detecting ransomware-specific indicators comparable to mass file modifications or unauthorized distant instruments, and sustaining remoted offline backups with examined restoration protocols additional bolster resilience.
Consumer coaching on phishing recognition and incident response simulations, built-in with community segmentation, ensures speedy containment, minimizing the extortion leverage of this more and more prolific menace actor.
As SafePay continues its unchecked growth, organizations should prioritize these technical safeguards to counter its autonomous, high-impact methodology.
Discover this Information Attention-grabbing! Comply with us on Google Information, LinkedIn, and X to Get Prompt Updates!

