A classy risk actor often called Curly COMrades has demonstrated superior evasion capabilities by leveraging legit Home windows virtualization options to ascertain covert, long-term entry to sufferer networks.
Working to assist Russian geopolitical pursuits, the group has deployed revolutionary instruments and strategies that efficiently bypass conventional endpoint detection and response (EDR) options.
This investigation, performed in collaboration with the Georgian CERT underneath the Operative-Technical Company of Georgia, reveals a multi-layered assault framework centered on Hyper-V abuse and customized malware implants.
Essentially the most notable discovery on this marketing campaign includes the exploitation of Hyper-V, Home windows’ native virtualization platform, to create an remoted assault infrastructure immediately on compromised machines.
Fairly than deploying malware immediately on the host working system, Curly COMrades enabled the Hyper-V function on chosen Home windows 10 techniques and deployed a minimalistic Alpine Linux-based digital machine containing their customized malware.
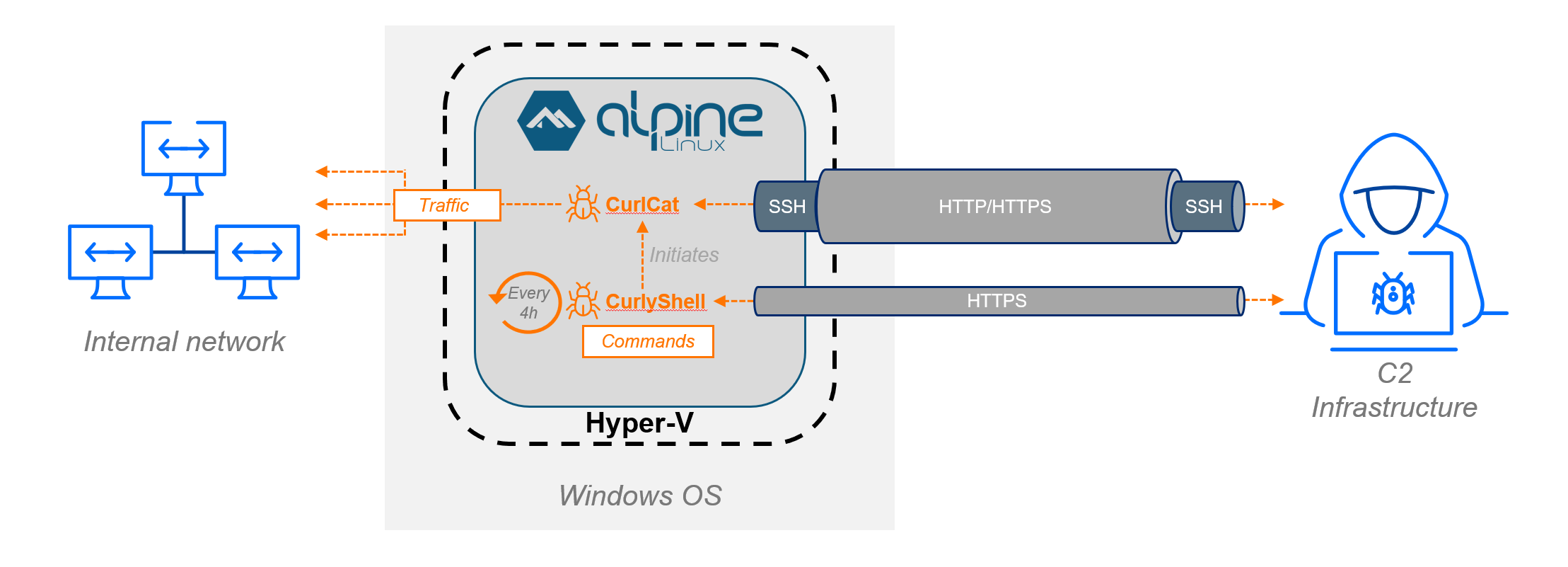
This surroundings occupied merely 120MB of disk area and consumed solely 256MB of reminiscence, creating a light-weight footprint that considerably reduces detection danger.
The attackers configured the digital machine to make use of Hyper-V’s Default Swap community adapter, which routes all site visitors via the host’s community stack utilizing Community Tackle Translation (NAT).
This intelligent configuration made all malicious outbound communication seem to originate from the legit host machine’s IP handle, successfully masking the true supply of assaults.
The VM itself was custom-made with attacker-controlled domain-to-IP mappings and personal DNS server configurations, enabling direct communication with command and management infrastructure whereas remaining remoted from conventional host-based monitoring.
Customized Malware Arsenal
Throughout the virtualized surroundings, Curly COMrades deployed two intently associated customized malware households: CurlyShell and CurlCat.
Each implants share an equivalent underlying code base written in C++ and constructed across the libcurl library, but serve distinctly totally different operational functions.
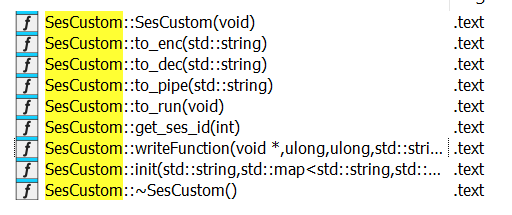
This system’s customized session administration begins with the development of the SesCustom object.

CurlyShell features as a persistent reverse shell, establishing and sustaining major connections to command and management infrastructure utilizing HTTPS.
The malware employs a non-standard Base64 encoding alphabet to evade safety instruments anticipating normal encoding patterns.
For persistence, it leverages a easy however efficient cron job executed at 20-minute intervals each 4 hours, guaranteeing steady entry even after system reboots.
CurlCat operates as a reverse proxy tunnel supervisor, designed particularly to wrap outgoing SSH site visitors into normal HTTP request payloads.
This method permits attackers to mix malicious communications with legit community site visitors, bypassing network-based detection techniques.
The malware integrates immediately into SSH consumer configurations, utilizing a ProxyCommand mechanism to covertly tunnel all subsequent connections via a SOCKS proxy on the attacker’s infrastructure.
PowerShell-Based mostly Lateral Motion
Past the virtualized surroundings, investigators found refined PowerShell scripts enabling lateral motion throughout compromised networks.
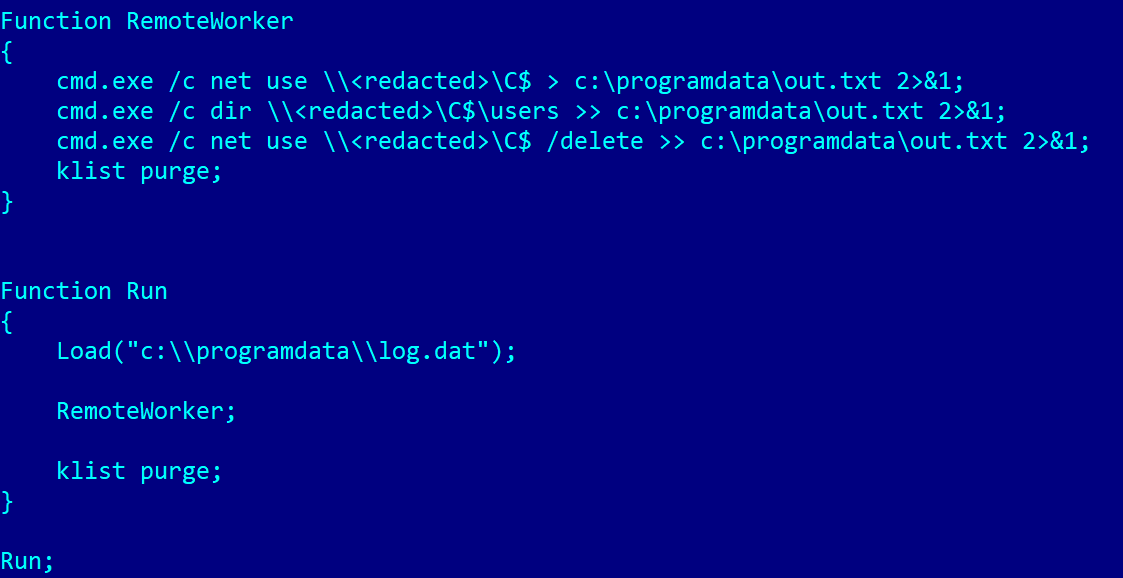
One script, discovered at c:programdatakb_upd.ps1, performs Kerberos ticket injection into the LSASS course of, permitting attackers to authenticate to distant techniques with out requiring passwords. The script encrypts embedded payloads utilizing a hardcoded key, demonstrating cautious operational safety concerns.
The RemoteWorker() operate is designed as a template for executing post-exploitation duties, utilizing the newly injected Kerberos tickets to authenticate towards distant techniques by way of SMB.

A second PowerShell variant found via Group Coverage deployment creates persistent native accounts on domain-joined machines.
Discovered at c:Windowsps1screensaver.ps1 and later variants, these scripts repeatedly reset account passwords to keep up persistent entry throughout remediation makes an attempt.
Crucial evaluation of the attackers’ command and management infrastructure grew to become attainable via swift collaboration between safety researchers and Georgian CERT officers.
When Georgian authorities seized a compromised web site used as a relay level, forensic evaluation revealed iptables guidelines redirecting sufferer site visitors to attacker infrastructure at 88.198.91[.]116, alongside customized sshd providers and application-level proxy configurations designed to reduce forensic traces.
The investigation demonstrates how trendy risk actors more and more abuse legit system options to evade detection, requiring organizations to implement defense-in-depth safety methods past conventional EDR options.
Observe us on Google Information, LinkedIn, and X to Get On the spot Updates and Set GBH as a Most popular Supply in Google.

