Within the ever-evolving panorama of cyber threats, a brand new ransomware pressure, Midnight, has emerged, echoing the infamous ways of its predecessor, Babuk.
First detected by Gen researchers, Midnight blends acquainted ransomware mechanics with novel cryptographic modifications—a few of which unintentionally open the door to file restoration.
This represents a uncommon alternative for victims to reclaim their information with out paying a ransom, marking a major breakthrough in ransomware protection capabilities.
Midnight exhibits clear indicators of being impressed by the Babuk ransomware household, which first appeared in early 2021 and shortly gained a fame for its aggressive ways and superior technical facets.
Babuk operated as a Ransomware-as-a-Service (RaaS), focusing on massive organizations throughout healthcare, finance, authorities, and different important infrastructure sectors.
The ransomware utilized sturdy encryption by HC256 and ECDH protocols alongside intermittent file encryption to maximise injury whereas sustaining operational pace.
In mid-2021, Babuk’s operators unexpectedly shut down and leaked their full supply code, together with builders for Home windows, ESXI, and NAS variants. This leak sparked a wave of impressed ransomware households, every modifying Babuk’s unique design to go well with their particular goals.
Cryptographic Weaknesses
Midnight retains a lot of Babuk’s core construction whereas introducing a number of modifications, most notably within the cryptographic scheme used for file encryption.
These adjustments, whereas probably supposed to enhance the ransomware’s effectiveness, inadvertently launched weaknesses that make file decryption potential beneath sure circumstances.
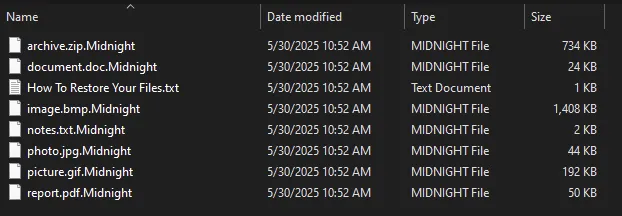
The ransomware usually appends the.Midnight or .endpoint extension to encrypted recordsdata, although in some configurations it appends the extension string on to the top of file content material reasonably than modifying filenames.
The cryptographic implementation makes use of ChaCha for encrypting file contents and RSA for encrypting the ChaCha20 key.
The RSA-encrypted key, together with its SHA256 hash, is appended to the top of every encrypted file in a constant format throughout identified samples.
To enhance efficiency, Midnight employs intermittent encryption, a way inherited from Babuk however refined by extra granular file size-based logic to find out which parts require encryption. This strategy permits sooner processing of huge recordsdata whereas rendering them unusable.
Figuring out Midnight Infections
Safety researchers have recognized a number of key indicators of Midnight an infection. The ransomware creates a mutex named “Mutexisfunnylocal” to forestall a number of situations from operating concurrently.
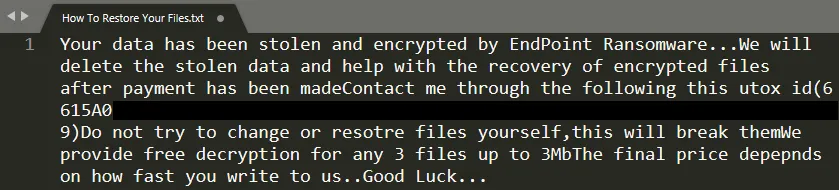

A ransom be aware named “How To Restore Your Recordsdata.txt” is dropped in affected directories. Some samples create debug logs recognized as both “Report.Midnight” or “debug.endpoint” relying on configuration.
Earlier Midnight variants primarily focused high-value recordsdata akin to databases, backups, and archives with extensions like .mdf, .ndf, .bak, .dbf, and .sql.
More moderen variants have broadened their scope, now encrypting practically all file varieties besides executables akin to .exe, .dll, and .msi recordsdata.

The ransomware accepts a number of command-line arguments for controlling conduct, together with choices to append extension strings to file content material, allow encryption of network-mounted volumes, and goal particular directories.
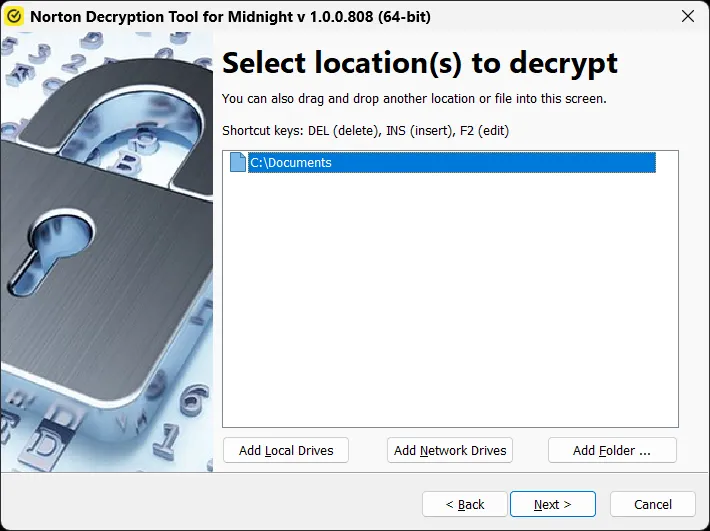
Safety distributors have launched decryption instruments particularly designed to deal with Midnight’s cryptographic flaws.
These decryptors information customers by a wizard-based course of to establish encrypted areas, confirm file integrity, and restore information with out requiring ransom cost.
Customers are suggested to run decryptors with administrator privileges and allow backup choices throughout the restoration course of, guaranteeing important safeguards stay in place all through decryption operations.
Observe us on Google Information, LinkedIn, and X to Get On the spot Updates and Set GBH as a Most popular Supply in Google.

