Cybersecurity researchers at Unit 42 have uncovered a classy Android spyware and adware marketing campaign that exploited a beforehand unknown zero-day vulnerability in Samsung Galaxy gadgets.
The malware, dubbed LANDFALL, leveraged a essential vulnerability in Samsung’s picture processing library to ship commercial-grade surveillance capabilities by maliciously crafted picture information despatched through WhatsApp.
The LANDFALL marketing campaign exploited CVE-2025-21042, a zero-day vulnerability in Samsung’s Android picture processing library that remained unpatched till April 2025.
Attackers embedded the spyware and adware inside malformed DNG (Digital Unfavourable) picture information, which had been delivered to targets by WhatsApp messages.
The exploitation technique carefully resembles an identical assault chain found concentrating on Apple iOS gadgets in August 2025, highlighting a broader sample of DNG picture processing vulnerabilities being weaponized throughout cell platforms.
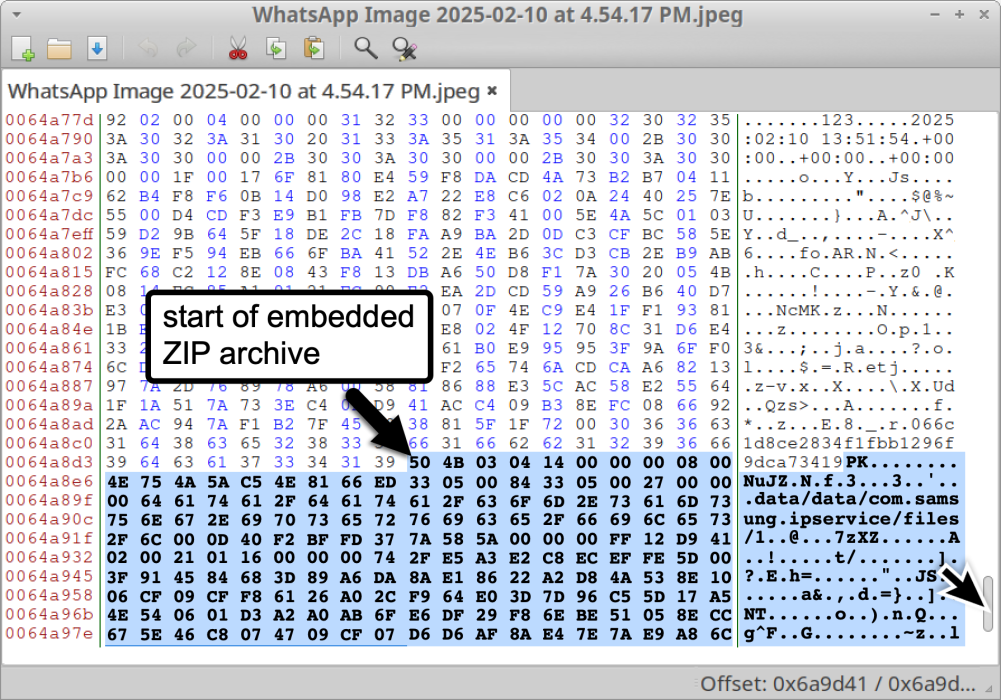
Unit 42’s discovery got here throughout their investigation of iOS exploit chains after they recognized a number of suspicious DNG information uploaded to VirusTotal all through 2024 and early 2025.
The filenames, equivalent to “WhatsApp Picture 2025-02-10 at 4.54.17 PM.jpeg” and “IMG-20240723-WA0000.jpg,” strongly recommend the malware was distributed by WhatsApp’s messaging platform. Importantly, researchers discovered no vulnerabilities in WhatsApp itself the applying was merely used as a supply mechanism.
Samsung 0-Day Vulnerability
LANDFALL is particularly designed to focus on Samsung Galaxy gadgets, together with the S22, S23, and S24 sequence, in addition to Z Fold4 and Z Flip4 fashions.
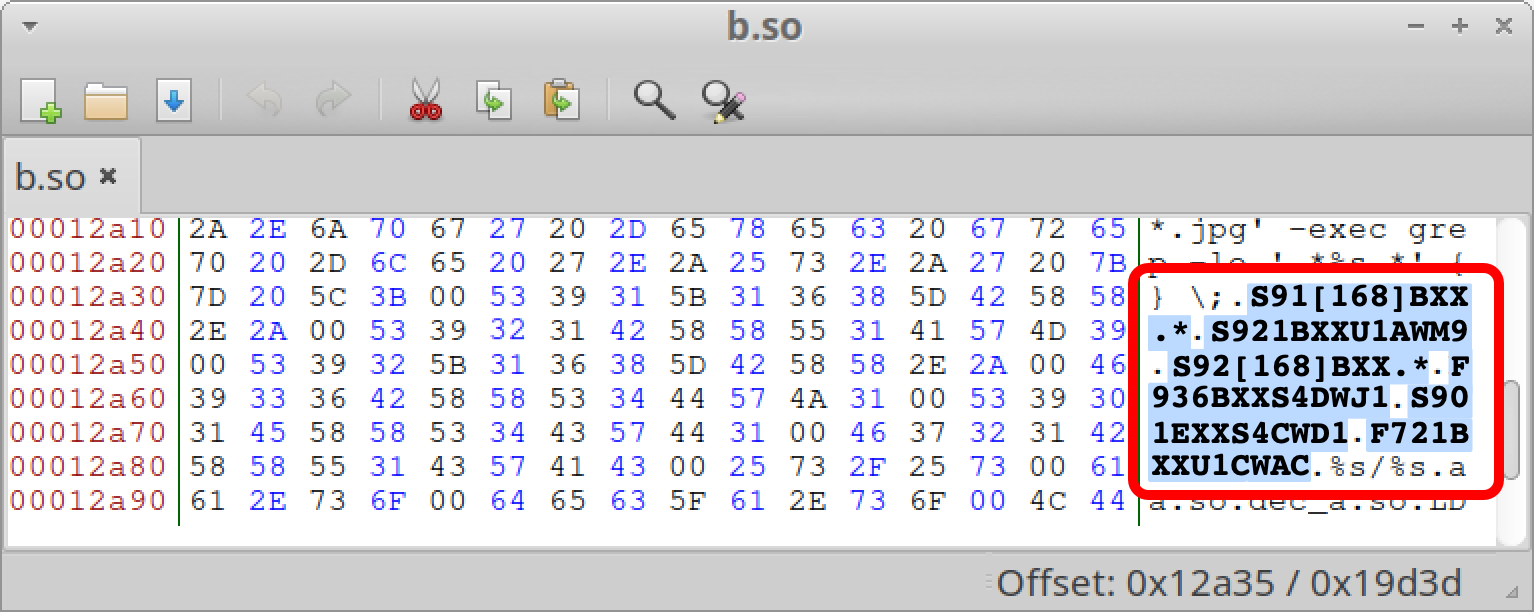
The b.so element of LANDFALL communicates with its C2 server over HTTPS utilizing a non-standard, ephemeral TCP port.

The spyware and adware permits in depth surveillance capabilities, together with microphone recording, location monitoring, name log assortment, and extraction of photographs, contacts, and SMS messages. Its modular structure suggests it might obtain further parts to increase its performance.
The malware’s loader element, internally known as “Bridge Head,” comprises subtle evasion methods to keep away from detection by safety instruments and debugging frameworks.
Evaluation revealed the spyware and adware might manipulate Android’s SELinux safety insurance policies to take care of elevated permissions and set up persistence on contaminated gadgets.
Proof signifies LANDFALL was deployed in focused intrusion actions inside the Center East, with potential victims recognized in Iraq, Iran, Turkey, and Morocco.
The marketing campaign’s infrastructure and tradecraft patterns share similarities with industrial spyware and adware operations related to non-public sector offensive actors (PSOAs) entities that develop and promote surveillance instruments to authorities shoppers.
Researchers famous potential connections to the Stealth Falcon menace group and potential hyperlinks to the Variston spyware and adware framework, which reportedly operated out of Barcelona earlier than ceasing operations in early 2025.
The b.so file’s configuration is managed by a mixture of hard-coded default values and an encrypted JSON object embedded inside itself.
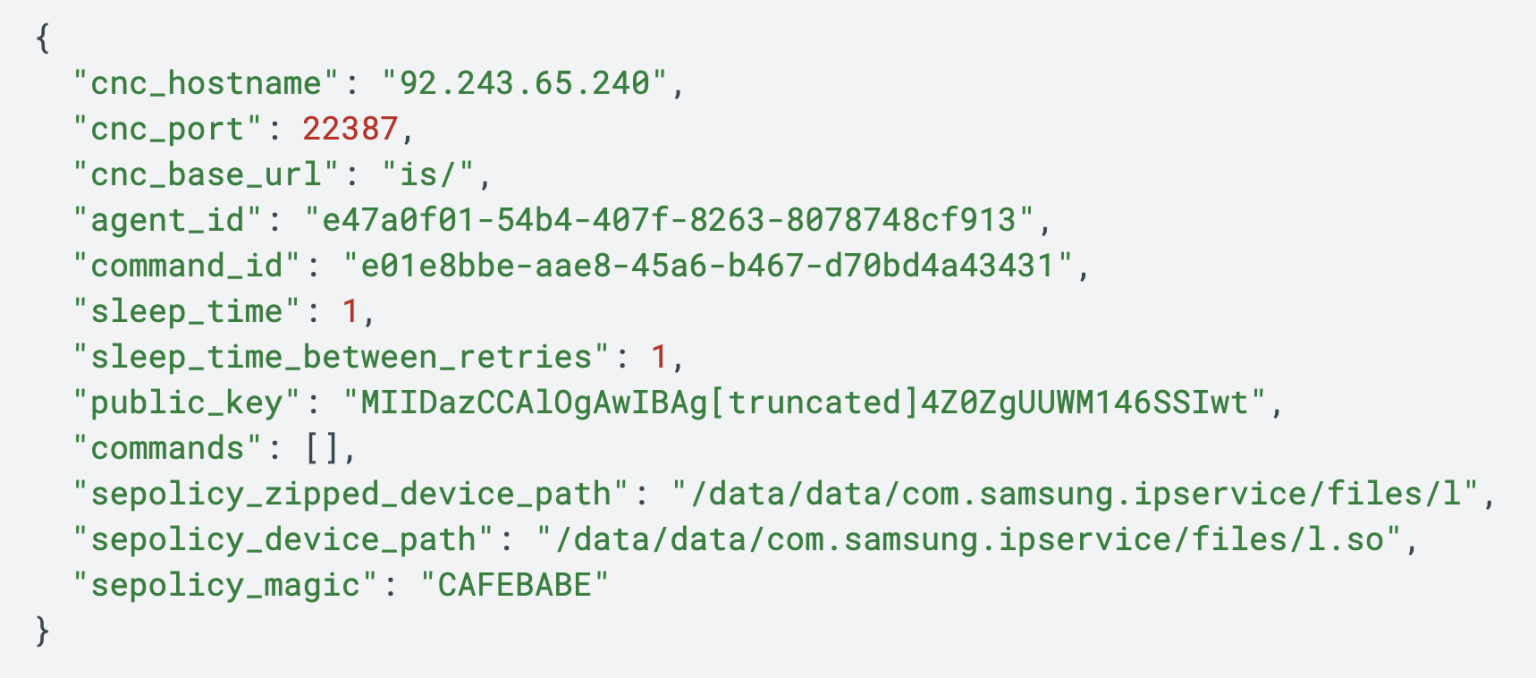

The “Bridge Head” naming conference utilized by LANDFALL matches terminology employed by a number of recognized industrial spyware and adware distributors, together with NSO Group and Variston.
Timeline and Present Standing
Unit 42 tracks this exercise as CL-UNK-1054 and continues investigating the marketing campaign’s scope and attribution. Palo Alto Networks prospects obtain safety by Superior WildFire, Superior URL Filtering, Superior DNS Safety, and Superior Risk Prevention merchandise, which have been up to date to detect LANDFALL-related indicators.
The earliest LANDFALL samples appeared in July 2024, months earlier than Samsung addressed the vulnerability in April 2025.
In September 2025, Samsung patched a further associated vulnerability, CVE-2025-21043, additional defending customers from related assault vectors. Samsung customers who’ve utilized safety updates since April 2025 are not in danger from this particular exploit.
Indicators of Compromise
| SHA256 Hash | Filename | Dimension |
|---|---|---|
| b06dec10e8ad0005ebb9da24204c96cb2e297bd8d418bc1c8983d066c0997756 | img-20250120-wa0005.jpg | 6.66 MB |
| c0f30c2a2d6f95b57128e78dc0b7180e69315057e62809de1926b75f86516b2e | 2.tiff | 6.58 MB |
| 9297888746158e38d320b05b27b0032b2cc29231be8990d87bc46f1e06456f93 | whatsapp picture 2025-02-10 at 4.54.17 pm.jpeg | 6.66 MB |
| d2fafc7100f33a11089e98b660a85bd479eab761b137cca83b1f6d19629dd3b0 | b.so | 103.31 KB |
| 384f073d3d51e0f2e1586b6050af62de886ff448735d963dfc026580096d81bd | (unknown) | 103.31 KB |
| b975b499baa3119ac5c2b3379306d4e50b9610e9bba3e56de7dfd3927a96032d | 1.jpeg | 5.66 MB |
| a62a2400bf93ed84ebadf22b441924f904d3fcda7d1507ba309a4b1801d44495 | (unknown) | 103.31 KB |
| 29882a3c426273a7302e852aa77662e168b6d44dcebfca53757e29a9cdf02483 | img-20240723-wa0001.jpg | 6.58 MB |
| 2425f15eb542fca82892fd107ac19d63d4d112ddbfe698650f0c25acf6f8d78a | 6357fc.zip | 380.71 KB |
| b45817ffb0355badcc89f2d7d48eecf00ebdf2b966ac986514f9d971f6c57d18 | img-20240723-wa0000.jpg | 5.65 MB |
| 69cf56ac6f3888efa7a1306977f431fd1edb369a5fd4591ce37b72b7e01955ee | localfile~ | 1.42 MB |
| 211311468f3673f005031d5f77d4d716e80cbf3c1f0bb1f148f2200920513261 | l | 332.88 KB |
| ffeeb0356abb56c5084756a5ab0a39002832403bca5290bb6d794d14b642ffe2 | (unknown) | 103.31 KB |
Observe us on Google Information, LinkedIn, and X to Get Prompt Updates and Set GBH as a Most well-liked Supply in Google.

