Risk researchers have uncovered a classy cell malware marketing campaign attributed to North Korea-linked risk actor Kimsuky, leveraging weaponized QR codes and fraudulent supply service impersonations to trick customers into putting in distant entry trojans on their smartphones.
The ENKI WhiteHat Risk Analysis Group recognized the newest iteration of “DOCSWAP” malware being distributed via an intricate social engineering scheme that begins with phishing messages containing malicious URLs.
When customers entry these hyperlinks from private computer systems, they obtain QR codes prompting them to modify to cell units for viewing.
The QR codes finally redirect victims to distribution servers internet hosting malicious Android functions disguised as respectable providers.
Leveraging APK metadata and infrastructure overlaps, we recognized three extra malicious functions and 7 C&C servers.
The distribution workflow employed server-side logic to detect the person’s gadget kind, displaying safety warnings and obtain prompts solely to Android customers whereas blocking entry from desktop browsers.
QR Code Assault Marketing campaign
When victims clicked the “Set up safety app” button, the server initiated an APK obtain whereas concurrently logging entry makes an attempt and transmission particulars to monitoring databases.
Safety researchers confirmed that attackers distributed the malware from infrastructure positioned at 27.102.137[.]181, creating faux supply monitoring pages that impersonated main logistics firms, together with CJ Logistics.

The malicious utility, named “SecDelivery.apk,” implements a classy two-stage an infection mechanism.
Upon execution, it decrypts an embedded encrypted APK file utilizing a newly developed native decryption operate slightly than the Java-based XOR decryption employed in earlier DOCSWAP variants.
This advanced strategy applies a number of obfuscation layers together with bit inversion, 5-bit rotation, and XOR encryption with a 4-byte key, considerably growing detection evasion capabilities.
The decrypted payload launches a persistent malicious service that gives full distant entry trojan performance.
The malware requests an intensive array of harmful permissions together with file system entry, SMS interception, telephone state monitoring, and background service execution capabilities.
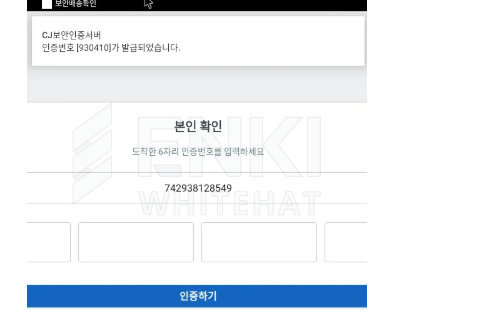
Notably, the appliance shows a faux authentication display screen masquerading as an over-the-top verification system, requesting a hardcoded supply monitoring quantity to keep up the deception whereas customers execute the malicious payload within the background.
The decrypted inside APK establishes command and management connections to the distribution server, implementing 57 distinct instructions enabling attackers to steal delicate information, file audio, seize keystrokes, and management contaminated units remotely.
When the app runs, SplashActivity masses the encrypted sources embedded within the APK, obtains the assorted permissions required for malicious conduct.
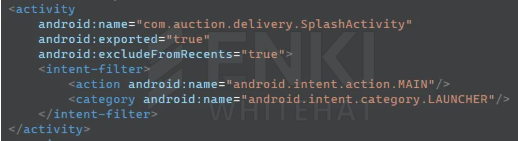
Researchers recognized a number of indicators conclusively attributing this marketing campaign to Kimsuky, together with the presence of the “Million OK!!!!” signature string beforehand related to the risk group’s phishing infrastructure.
Potential Dangers and Affect
The investigation revealed infrastructure overlap with identified Kimsuky Naver phishing campaigns, an identical parameter constructions, and shared command and management server infrastructure.
Supply quantity is hardcoded throughout the APK as “742938128549”, and we assess the risk actor possible delivered it alongside the malicious URL through the preliminary entry part.
Moreover, embedded Korean-language feedback throughout the malware code and distribution web sites together with phrases like “go away log when button is clicked” and “APK obtain began” strongly point out the risk actors’ Korean language proficiency and ties to North Korean operations.
The excellent evaluation uncovered seven extra command and management servers using an identical JARM fingerprints, in addition to three extra malicious functions disguised as supply providers, cryptocurrency airdrops, and VPN functions.
Researchers additionally documented proxy-based phishing websites harvesting Naver and Kakao credentials from victims via refined login credential interception routines.
Safety professionals advocate customers confirm hyperlink locations earlier than clicking, notably from unknown senders, and undertake conservative analysis of app permission requests.
Organizations ought to implement cell risk detection options, implement utility vetting insurance policies, and educate workers concerning refined phishing strategies concentrating on cell platforms.
The marketing campaign demonstrates evolving North Korean capabilities in cell exploitation and underscores the important significance of cell safety consciousness throughout enterprise and client environments.
Comply with us on Google Information, LinkedIn, and X to Get Immediate Updates and Set GBH as a Most popular Supply in Google.

