Tax-themed phishing campaigns have intensified in latest months, capitalizing on the heightened consciousness surrounding India’s Earnings Tax Return (ITR) submitting season.
Public discussions about refund timelines and compliance deadlines create a really perfect backdrop for attackers to craft credible lures.
Current evaluation of emails impersonating the Indian Earnings Tax Division reveals a classy operation way more harmful than typical credential-harvesting schemes a coordinated multi-stage an infection chain designed to ascertain persistent distant entry to sufferer techniques.
The assault begins with a rigorously crafted spear-phishing e-mail spoofed from an Outlook.com area, a right away purple flag since professional authorities companies keep away from public webmail companies.
The topic line, “Tax Compliance Overview Discover,” exploits recipient considerations about missed deadlines.
Somewhat than utilizing text-based content material that automated filters would possibly detect, attackers embedded a picture replicating an genuine ITD discover, full with the Authorities of India emblem, fabricated workplace references, pretend DIN numbers, and synthetic urgency markers.
The hooked up “Overview Annexure.pdf” escalates the social engineering stress by claiming prior non-compliance and directing customers to a fraudulent “Compliance Portal” through an embedded URL.
This narrative development notification of alleged violation adopted by a corrective motion hyperlink represents textbook psychological manipulation designed to bypass important pondering in time-pressured recipients.
The An infection Cascade
Notably, the portal shows an explicitly suspicious message: “To keep away from false positives from safety software program, please disable your antivirus program prematurely earlier than utilizing the shopper.”
No professional authorities service would request this a clear sign of malicious intent that makes an attempt to decrease sufferer defenses by way of a false “compatibility” clarification.
The extracted executable, a 150MB NSIS installer digitally signed by a Chinese language entity (Hengshui Shenwei Expertise Co., Ltd.), operates as a silent loader.
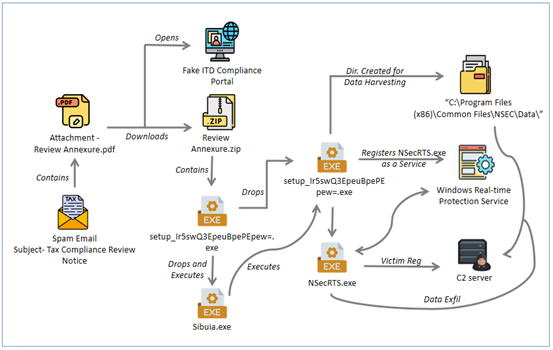
It unpacks a number of elements into momentary directories, executes supporting binaries with out consumer interplay, after which self-destructs to attenuate forensic proof.
This handoff mechanism introduces a second-stage installer an extra 147MB NSIS bundle with a unique digital signature (Shandong Anzai Info Expertise CO., Ltd.); this successfully creates a two-layer deployment structure that complicates attribution and detection.
The second stage installs a Chinese language-language utility bundle that extracts kernel drivers, distant desktop elements, system utilities, and monitoring instruments into “C:Program FilesCommon FilesNSEC” with hidden attributes.
The installer then achieves persistence by registering NSecRTS.exe as a Home windows Service masquerading as “Home windows Actual-time Safety Service,” guaranteeing computerized execution at system startup.
The NSecRTS.exe service establishes encrypted command-and-control (C2) connections to a number of IP addresses (154[.]91[.]84[.]3, 45[.]113[.]192[.]102, and 103[.]235[.]46[.]102) throughout non-standard ports, enabling distant job execution and extra payload deployment.
Risk Implications
This marketing campaign exemplifies a elementary shift in tax-themed phishing: past credential theft, it delivers full-featured Distant Entry Trojan capabilities with persistent entry, intensive surveillance, and command-and-control infrastructure.
Sibuia.exe spawns one other “setup_Ir5swQ3EpeuBpePEpew=.exe” as a toddler course of from the momentary � listing, successfully handing off execution to the one other signed installer payload.

As soon as persistence is established, the malware begins harvesting intensive system info OS model, put in functions, operating companies, and {hardware} configuration storing this information in a structured listing format.
A number of technical indicators Simplified Chinese language language utilization, installer ecosystem structure, and code-signing entities recommend China-linked growth or packaging.
For defenders, the lesson is obvious: finance-themed phishing emails stay efficient social engineering vectors exactly as a result of they exploit professional seasonal considerations.
Organizations should implement e-mail filtering past textual content evaluation, scrutinize suspicious requests to show off safety controls, and monitor for unauthorized service registrations and non-standard C2 communications.
Comply with us on Google Information, LinkedIn, and X to Get Instantaneous Updates and Set GBH as a Most popular Supply in Google.

