Illicit cryptocurrency transactions reached unprecedented ranges in 2025 as nation-states weaponized digital belongings to evade sanctions, reworking the cybercrime panorama right into a geopolitical battleground with record-breaking monetary volumes.
In keeping with blockchain evaluation knowledge, illicit cryptocurrency addresses acquired no less than $154 billion in 2025, representing a 162% year-over-year enhance that establishes a brand new benchmark for digital finance.
Illicit cryptocurrency transactions reached unprecedented ranges in 2025 as nation-states weaponized digital belongings to evade sanctions, reworking the cybercrime panorama right into a geopolitical battleground with record-breaking monetary volumes.
In keeping with blockchain evaluation knowledge, illicit cryptocurrency addresses acquired no less than $154 billion in 2025, representing a 162% year-over-year enhance that establishes a brand new benchmark for digital monetary crime.
This surge was primarily pushed by a dramatic 694% enhance in worth acquired by sanctioned entities, although even with out this spike, 2025 would have set information throughout practically each class of crypto-related crime.
Nation-State Threats Drive File Volumes
North Korean cyber operatives intensified their cryptocurrency heists to unprecedented ranges, stealing $2 billion by subtle assaults.
This infrastructure, constructed on 2024 laws designed to facilitate sanctions evasion, demonstrates how state actors are creating bespoke blockchain programs to bypass worldwide monetary restrictions at scale.
The February Bybit exploit, which netted practically $1.5 billion, stands as the biggest digital heist in cryptocurrency historical past and exemplifies the regime’s evolving capabilities.
For the previous few years, stablecoins have come to dominate the panorama of illicit transactions, and now account for 84% of all illicit transaction quantity.
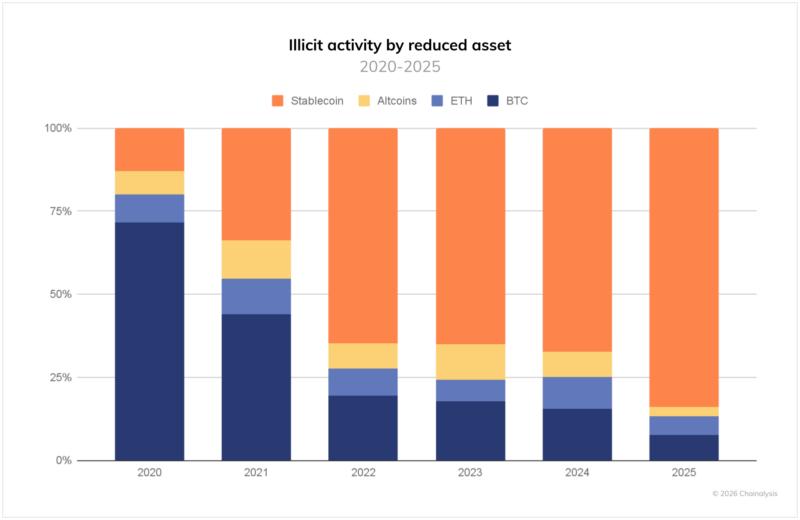
These operations now function superior intrusion and laundering techniques that outpace earlier years in each sophistication and harmful affect.
Russia’s sanctioned crypto economic system achieved huge scale with the February 2025 launch of the ruble-backed A7A5 token, which transacted over $93.3 billion in lower than twelve months.
Iranian proxy networks continued their on-chain operations, facilitating $2+ billion in cash laundering, illicit oil gross sales, and arms procurement by cryptocurrency wallets recognized in sanctions designations.
Iran-aligned terrorist organizations together with Lebanese Hezbollah, Hamas, and the Houthis have expanded their crypto utilization to unprecedented ranges regardless of army setbacks.
2025 witnessed the emergence of Chinese language Cash Laundering Networks (CMLNs) because the dominant pressure in illicit on-chain ecosystems.
These subtle operations have professionalized crypto crime by providing specialised providers together with laundering-as-a-service and felony infrastructure assist.
Constructing on frameworks established by operations like Huione Assure, CMLNs have created full-service felony enterprises that assist every little thing from fraud and scams to North Korean hacking proceeds, sanctions evasion, and terrorist financing.
Full-Stack Illicit Infrastructure
Whereas nation-state exercise captures headlines, conventional cybercrime stays sturdy. Ransomware operators, malware distributors, and illicit marketplaces more and more depend upon built-in infrastructure suppliers providing area registration, bulletproof internet hosting, and technical providers designed to face up to takedowns and sanctions enforcement.
These platforms have developed from area of interest resellers into complete infrastructure ecosystems that assist each financially motivated criminals and state-aligned actors, amplifying the attain and resilience of malicious cyber exercise.
The digital nature of cryptocurrency crime is more and more intersecting with bodily violence. Human trafficking operations have expanded their crypto utilization.
On the similar time, bodily coercion assaults the place criminals use violence to pressure victims to switch digital belongings have risen disturbingly, typically timed to coincide with cryptocurrency worth peaks.
This convergence of digital and bodily threats represents a harmful evolution in crypto-enabled crime.
Observe us on Google Information, LinkedIn, and X to Get Immediate Updates and Set GBH as a Most well-liked Supply in Google.

