Current findings from the analysis agency Recorded Future’s Insikt Group reveal that it solely takes two seconds of distraction for an expert’s personal knowledge to fall into the mistaken arms.
In line with Recorded Future’s newest weblog publish, a Russian state-sponsored hacking group, referred to as BlueDelta (or Fancy Bear), has been finishing up sneaky campaigns to steal login info from professionals worldwide.
Reportedly, betweet Feburary and September 2025, BlueDelta focused people is specialised frields like power and nuclear analysis, significantly in Türkiye and Europe. Researchers noticed that the marketing campaign’s goal appears to be credentials harvesting.
How the Scams Work
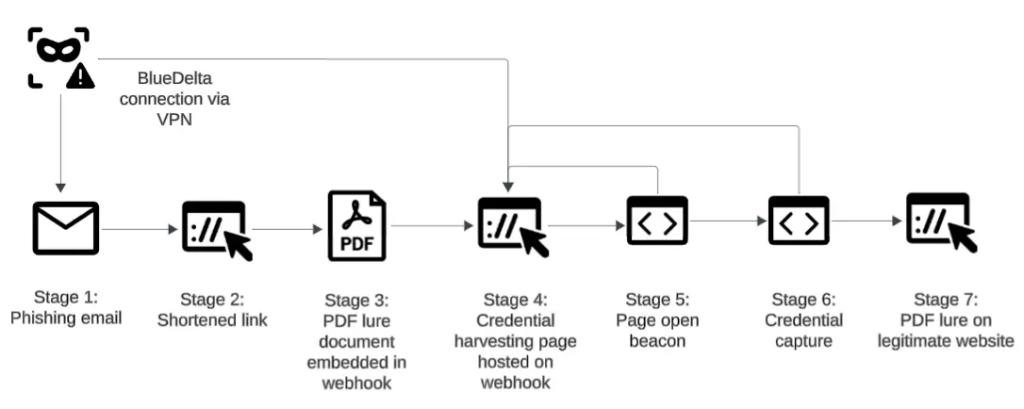
Researchers famous that the hackers have gotten far more convincing as a result of, as an alternative of utilizing apparent faux hyperlinks, they present the sufferer an actual doc first. For instance, a goal might obtain a hyperlink that opens a legitimate-looking PDF about local weather change or worldwide politics, reminiscent of a report from the Gulf Analysis Centre (GRC) concerning Israel and Iran.
One other such lure was a report from the EcoClimate Basis titled “Local weather Motion as a Strategic Precedence,” which particularly focused scientists engaged on renewable power. Whereas the sufferer is distracted by these paperwork, the web site is definitely working within the background. After simply two seconds, the web page mechanically switches to a faux login display.
Additional investigation revealed that these faux pages have been designed to seem like:
- Google: Utilizing Portuguese-language pages to trick customers.
- Sophos VPN: Aimed toward employees inside a European assume tank.
- Microsoft Outlook (OWA): Particularly focusing on army employees in North Macedonia and IT consultants in Uzbekistan.
Easy however Efficient Techniques
It’s price noting that BlueDelta doesn’t use costly gear for these assaults; they depend on free web companies like Webhook.web site, ngrok, and InfinityFree. In line with researchers, this makes the assaults a “low-cost, high-yield” method to steal knowledge as a result of when a sufferer enters their particulars, the hackers’ code mechanically saves the information after which sends the consumer again to the true web site.
“The usage of Turkish-language and regionally focused lure materials means that BlueDelta tailor-made its content material to extend credibility,” the weblog publish reads. By the point the sufferer is redirected to the true login web page, their credentials have already been stolen.
This exercise represents a significant enlargement of BlueDelta’s operations, exhibiting their dedication to accumulating info from authorities and analysis networks.
That’s why, consultants urge you to at all times examine hyperlinks for suspicious addresses like webhook.web site, and by no means belief login prompts that seem all of the sudden whereas studying a PDF. It additionally helps to make sure you have multi-factor authentication energetic on all skilled accounts to remain protected.
(Picture by KOBU Company on Unsplash)