A newly analyzed marketing campaign dubbed “Evelyn Stealer” is popping the Visible Studio Code (VSC) extension ecosystem into an assault supply platform, enabling risk actors to compromise software program builders and pivot deeper into enterprise environments.
The marketing campaign abuses seemingly respectable extensions together with a “Bitcoin Black” theme and a “Codo AI” coding assistant because the preliminary lure.
Whereas they current as a beauty theme and a purposeful AI helper, each extensions comprise hidden logic that executes PowerShell and batch scripts on activation, downloading and staging the malware within the background.
The operation, detailed by Koi Safety and TrendAI researchers, chains malicious VSC extensions, DLL hijacking, course of hollowing, and anti-analysis strategies right into a mature multi-stage information theft pipeline that immediately targets high-value developer workstations.
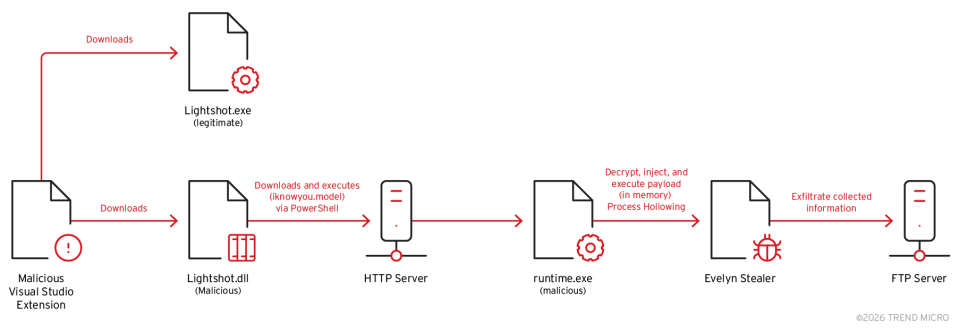
As soon as put in, the extensions ship the respectable Lightshot screenshot utility paired with a trojanized DLL, leveraging traditional DLL hijacking to execute attacker-controlled code underneath the guise of a trusted binary.
The primary-stage payload, Lightshot.dll, masquerades as a respectable Lightshot element and is sideloaded by Lightshot.exe.
When loaded, the DLL instantly runs its personal payload, exposing benign-looking exports to mix in and implementing a singleton-style mutex to make sure just one occasion executes on every host.
It then spawns a hidden PowerShell command to retrieve a second-stage executable into the person’s Temp listing as “runtime.exe,” establishing the muse for a deeper intrusion chain.
This second stage, recognized as iknowyou.mannequin, features as a process-hollowing injector. It creates a suspended occasion of the Home windows course of grpconv.exe and decrypts the embedded Evelyn Stealer payload utilizing AES‑256‑CBC, with hardcoded key and IV values.
After decryption, the malware replaces the reminiscence of the suspended grpconv.exe occasion with the Evelyn Stealer code and resumes execution, permitting the ultimate payload to function inside a respectable Home windows course of and evade primary behavioral and signature-based safety controls.
As soon as energetic, Evelyn Stealer dynamically resolves Home windows APIs for course of injection, file and registry operations, community communication, and clipboard entry.
The malware performs intensive atmosphere checks, together with GPU, hostname, disk dimension, course of, and registry evaluation, and incorporates digital machine and debugger detection to keep away from sandboxes and analysis environments.
If the system passes these checks, Evelyn creates its personal working listing within the person’s AppData path and begins harvesting information at scale.
The stealer focuses closely on browser-centric information theft and session hijacking. It restores and kills energetic browser processes, then launches new hidden browser cases (for instance, Chrome or Edge) with a protracted listing of flags resembling “–headless=new,” “–no-sandbox,” “–disable-extensions,” “–disable-logging,” and off-screen, 1×1-pixel home windows to reduce person visibility and forensic traces.
A devoted browser injection DLL, abe_decrypt.dll, is fetched from the Temp listing, the attacker’s FTP server, or the present working listing and injected to extract credentials, cookies, and session information.
Browser information, Evelyn Stealer captures clipboard contents, saved Wi‑Fi credentials, system data, put in software program lists, operating processes, VPN configuration, and a number of classes of cryptocurrency pockets information.
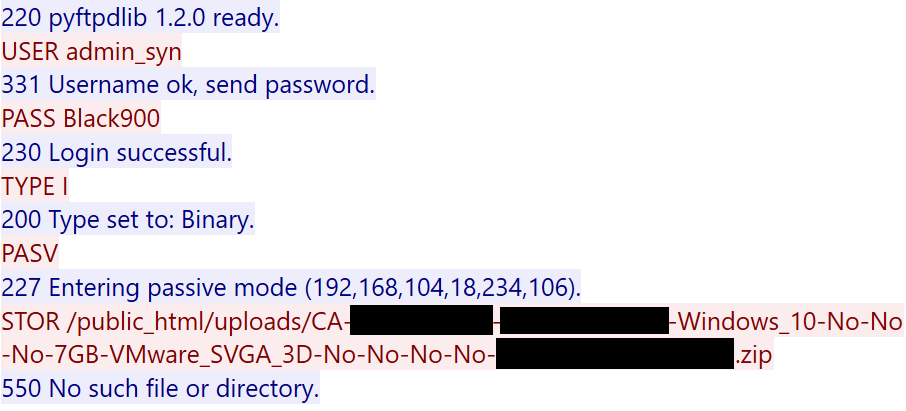
Collected artifacts are staged right into a ZIP archive whose filename encodes wealthy context, together with nation, IP deal with, username, OS model, {hardware} data, and wallet-related flags, earlier than being exfiltrated over FTP to attacker-controlled infrastructure.
Mitigations
The risk has clear implications for organizations that depend on VSC and third-party extensions throughout improvement, DevOps, and manufacturing environments.
As soon as the malware collects all the required data, it archives the info right into a ZIP file and sends it to the attacker’s C&C server over FTP.
Compromised developer machines present adversaries with direct entry to supply code, secrets and techniques, CI/CD pipelines, cloud consoles, and digital property resembling cryptocurrency.
The Evelyn marketing campaign demonstrates how attackers are operationalizing belief in developer instruments and marketplaces, iterating on social engineering themes (darkish crypto-inspired themes, AI copilots) whereas refining their supply chain.
Distributors resembling TrendAI Imaginative and prescient One™ report detection and blocking protection for Evelyn-related indicators of compromise and supply searching queries and risk intelligence to assist defenders determine malicious extensions, payloads, and C2 infrastructure.
For enterprises, the marketing campaign underscores the urgency of treating developer environments as high-risk property: implementing strict extension vetting, monitoring for anomalous PowerShell and headless browser exercise, hardening in opposition to DLL hijacking, and making use of zero-trust rules to improvement and construct methods.
As AI-powered assistants and wealthy extension ecosystems proliferate in IDEs, comparable campaigns weaponizing developer tooling are prone to speed up, making proactive controls and steady monitoring important to defending each code and demanding enterprise infrastructure.
Observe us on Google Information, LinkedIn, and X to Get Instantaneous Updates and Set GBH as a Most well-liked Supply in Google.

