2025 could also be remembered because the 12 months that hacktivist assaults turned considerably extra harmful.
Hacktivists moved properly past their conventional DDoS assaults and web site defacements in 2025, more and more focusing on industrial management programs (ICS), ransomware, breaches, and information leaks, as their sophistication and alignment with nation-state pursuits grew.
That was one of many conclusions in Cyble’s exhaustive new 2025 Menace Panorama report, from which this weblog was tailored.
Waiting for 2026 and past, Cyble expects important infrastructure assaults by hacktivists to proceed to develop, rising use of customized instruments by hacktivists, and deepening alignment between nation-state pursuits and hacktivists.
ICS Assaults by Hacktivists Surge
Between December 2024 and December 2025, a number of hacktivist teams elevated their concentrate on ICS and operational expertise (OT) assaults. Z-Pentest was essentially the most energetic actor, conducting repeated intrusions in opposition to a variety of commercial applied sciences. Darkish Engine (Infrastructure Destruction Squad) and Sector 16 persistently focused ICS, primarily exposing Human Machine Interfaces (HMI).
A secondary tier of teams, together with Golden Falcon Staff, NoName057 (16), TwoNet, RipperSec, and Inteid, additionally claimed to have carried out recurrent ICS-disrupting assaults, albeit on a smaller scale.
HMI and web-based Supervisory Management and Information Acquisition (SCADA) interfaces had been the most ceaselessly focused programs, adopted by a restricted variety of Digital Community Computing (VNC) compromises, which posed the best operational dangers to a number of industries.
Constructing Administration System (BMS) platforms and Web of Issues (IoT) or edge-layer controllers had been additionally focused in rising numbers, reflecting the broader exploitation of weakly secured IoT interfaces.
Europe remained the first area affected by pro-Russian hacktivist teams, with sustained focusing on of Spain, Italy, the Czech Republic, France, Poland, and Ukraine contributing to the best focus of ICS-related intrusions.
The Intersection of State Pursuits and Hacktivism
State-aligned hacktivist exercise remained persistent all through 2025. Operation Eastwood (14–17 July) disrupted NoName057(16)’s DDoS infrastructure, prompting swift retaliatory assaults from the hacktivist group. The group quickly rebuilt capability and resumed operations in opposition to Ukraine, the EU, and NATO, underscoring the resilience of state-directed ecosystems.
U.S. indictments and sanctions additional uncovered alleged structured cooperation between Russian intelligence providers and pro-Kremlin hacktivist fronts. The Justice Division detailed GRU-backed financing and tasking of the Cyber Military of Russia Reborn (CARR), in addition to the state-sanctioned improvement of NoName057(16)’s DDoSia platform.
Z-Pentest, recognized as a part of the identical CARR ecosystem and attributed to GRU, continued focusing on EU and NATO important infrastructure, reinforcing the convergence of activist personas, state mandates, and operational doctrine.
Professional-Ukrainian hacktivist teams, although not formally state-directed, carried out sustained, damaging operations in opposition to networks linked to the Russian army. The BO Staff and the Ukrainian Cyber Alliance carried out a number of information destruction and wiper assaults, encrypting key Russian companies and state equipment. Ukrainian actors repeatedly acknowledged that exfiltrated datasets had been handed to nationwide intelligence providers.
Hacktivist teams Cyber Partisans BY (Belarus) and Silent Crow claimed a year-long Tier-0 compromise of Aeroflot’s IT setting, allegedly exfiltrating greater than 20TB of information, sabotaging hundreds of servers, and disrupting core airline programs, a breach that Russia’s Normal Prosecutor confirmed brought about important operational outages and flight cancellations.
Analysis into BQT.Lock (BaqiyatLock) suggests a believable ideological alignment with Hezbollah, as evidenced by narrative framing and focusing on posture. Nonetheless, no verifiable technical proof has confirmed a direct organizational hyperlink.
Cyb3r Av3ngers, related to the Islamic Revolutionary Guard Corps (IRGC), struck important infrastructure property, together with electrical networks and water utilities in Israel, the USA, and Eire. After being banned on Telegram, the group resurfaced beneath the alias Mr. Soul Staff.
Tooling and functionality improvement by hacktivist teams additionally grew considerably in 2025. Noticed actions have included:
- Notable development in customized software creation (e.g., BQT Locker and related utilities), together with the adoption of ransomware as a hacktivist mechanism.
- Actors are more and more utilizing AI-generated textual content and imagery for propaganda and spreading misinformation and disinformation.
- Software promotion and advertising and marketing is turning into an rising driver fueling hacktivism.
Hacktivist Sightings Surged 51% in 2025
In 2025, hacktivism developed right into a globally coordinated risk, intently monitoring geopolitical flashpoints. Armed conflicts, elections, commerce disputes, and diplomatic crises fueled intensified campaigns in opposition to state establishments and significant infrastructure, with hacktivist teams weaponizing cyber-insurgency to advance their propaganda agendas.
Professional-Ukrainian, pro-Palestinian, pro-Iranian, and different nationalist teams launched ideologically pushed campaigns tied to the Russia-Ukraine Conflict, the Israel-Hamas battle, Iran-Israel tensions, South Asian tensions, and the Thailand-Cambodia border disaster. Home political unrest within the Philippines and Nepal triggered sustained assaults on authorities establishments.
Cyble recorded a 51% improve in hacktivist sightings in 2025, from 700,000 in 2024 to 1.06 million in 2025, with the majority of exercise centered on Asia and Europe (chart beneath).

Professional-Russian state-aligned hacktivists and pro-Palestinian, anti-Israel collectives continued to be the first drivers of hacktivist exercise all through 2025, shaping the operational tempo and geopolitical focus of the risk panorama.
Alongside these dominant ecosystems, Cyble noticed a marked improve in operations by Kurdish hacktivist teams and rising Cambodian clusters, each of which carried out campaigns intently aligned with regional strategic pursuits.
Under are a few of the main hacktivist teams of 2025:

India, Ukraine, and Israel had been the international locations most impacted by hacktivist exercise in 2025 (nation breakdown beneath).

Amongst world areas focused, Europe and NATO confronted a sustained pro-Russian marketing campaign marked by coordinated DDoS assaults, information leaks, and escalating ICS intrusions in opposition to NATO and EU member states. Authorities & LEA, Power & Utilities, Manufacturing, and Transportation had been constant targets.
Within the Center East, Israel stays the principal goal amid the Gaza conflict-related escalation, Iran-Israel confrontation, and Yemen-Saudi hostilities. Saudi Arabia, UAE, Egypt, Jordan, Iraq, Syria, and Yemen confronted sustained DDoS assaults, defacements, information leaks, and illicit entry to uncovered ICS property from ideologically aligned coalitions working throughout the area.
In South Asia, India-Pakistan and India-Bangladesh tensions fueled high-volume, ideologically framed offensives, peaking round political flashpoints and militant incidents. Exercise focused on Authorities & LEA, BFSI, Telecommunication, and Training.
In Southeast Asia, border tensions and home unrest formed a fragmented however energetic theatre: Thailand-Cambodia conflicts triggered reciprocal DDoS and defacements; Indonesia & Malaysia incidents stemmed from political and social disputes; the Philippines noticed assaults linked to inside instability; and Taiwan emerged as a recurring goal for pro-Russian actors.
Under are a few of the main hacktivist campaigns of 2025:

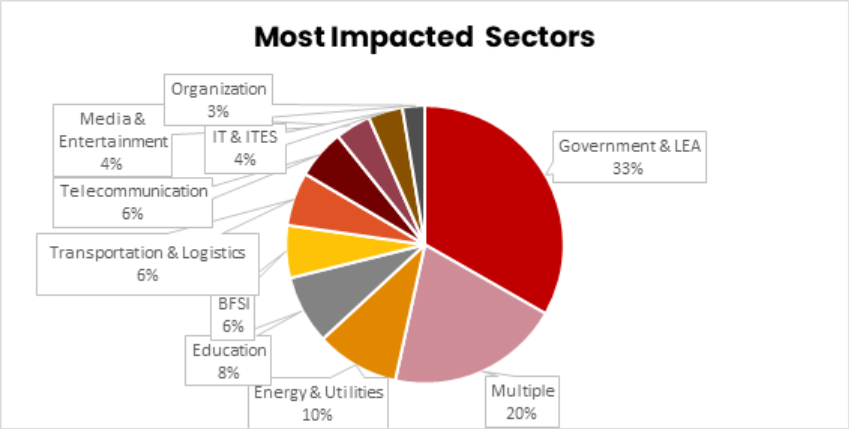
Most Impacted Industries and Sectors
2025 witnessed a marked growth of hacktivist focus throughout a number of industries. Authorities & LEA, Power & Utilities, Training, IT & ITES, Transportation & Logistics, and Manufacturing skilled essentially the most pronounced development in focusing on, driving the 12 months’s general improve in operational exercise.
The dataset additionally reveals a broadened assault floor, with a number of new or considerably expanded classes, together with Agriculture & Livestock, Meals & Drinks, Hospitality, Development, Automotive, and Actual Property.
Authorities & LEA was essentially the most impacted sector by a large margin, adopted by Power & Utilities (chart beneath).
The Evolution of Hacktivism
Hacktivism has developed right into a geopolitically charged, ICS-focused risk, persevering with to take advantage of uncovered OT environments and more and more weaponizing ransomware as a protest mechanism.
In 2026, hacktivists and cybercriminals will more and more goal uncovered HMI/SCADA programs and VNC takeovers, aided by public PoCs and automatic scanning templates, creating ripple results throughout the power, water, transportation, and healthcare sectors.
Hacktivists and state actors will more and more make use of financially motivated techniques and appearances. State actors in Iran, Russia, and North Korea will more and more undertake RaaS platforms to fund operations and preserve believable deniability. Crucial infrastructure assaults in Taiwan, the Baltic states, and South Korea will seem financially motivated whereas serving geopolitical goals, complicating attribution and response.
Crucial property needs to be remoted from the Web wherever attainable, and operational expertise (OT) and IT networks needs to be segmented and guarded with Zero Belief entry controls. Vulnerability administration, together with community and endpoint monitoring and hardening, is one other important cybersecurity finest observe.
Cyble’s complete assault floor administration options can assist by scanning community and cloud property for exposures and prioritizing fixes, along with monitoring for leaked credentials and different early warning indicators of main cyberattacks. Get a free exterior risk profile in your group right now.

