Ransomware teams have averaged practically 700 victims a month within the final 4 months, and lots of assaults have posed provide chain dangers.
Ransomware teams claimed greater than 2,000 assaults within the final three months of 2025 – and they’re beginning 2026 at the identical elevated tempo.
Cyble recorded 2,018 claimed assaults by ransomware teams within the fourth quarter of 2025, a mean of slightly below 673 a month. The menace teams maintained that tempo in January 2026, claiming 679 ransomware victims.
By comparability, within the first 9 months of 2025, ransomware teams averaged 512 claimed victims a month, so the pattern within the final 4 months has been greater than 30% above the earlier nine-month interval. The chart beneath reveals ransomware assaults by month since 2021.
Qilin Leads All Ransomware Teams as CL0P Returns
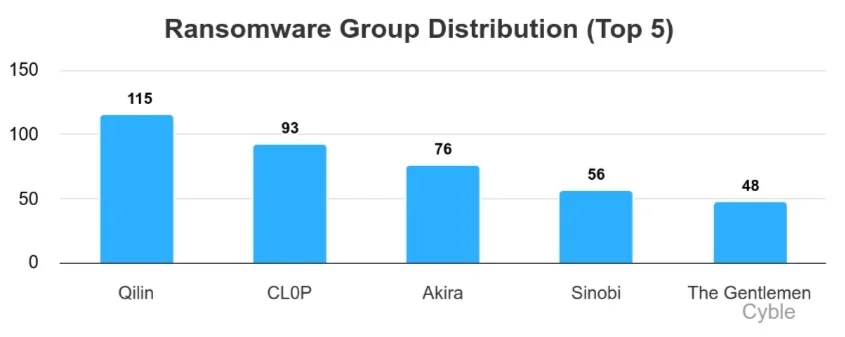
Qilin as soon as once more led all ransomware teams, with 115 claimed assaults in January. A resurgent CL0P has claimed scores of victims within the final two weeks, but as of this writing had offered no technical particulars on the group’s newest marketing campaign. Akira as soon as once more remained among the many leaders with 76 claimed victims, whereas newcomers Sinobi and The Gents rounded out the highest 5 (chart beneath).
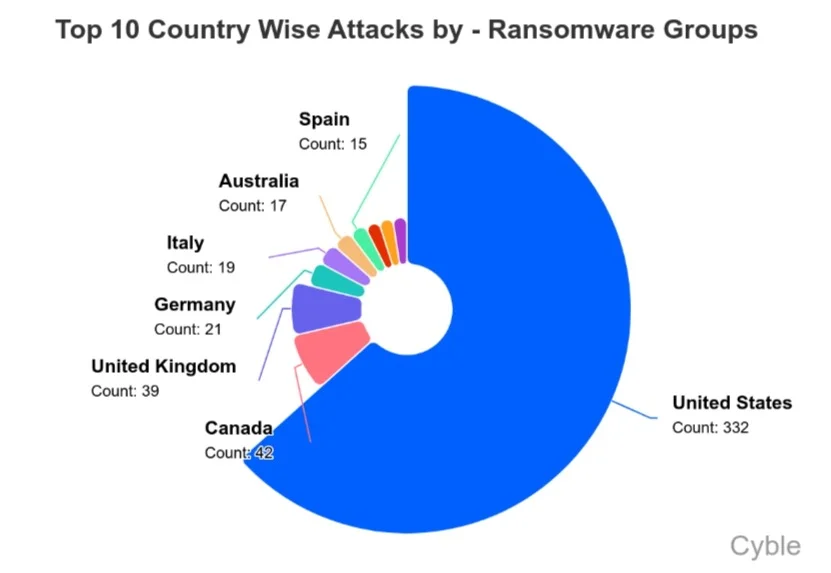
The U.S. as soon as once more was probably the most attacked nation by a big margin, accounting for slightly below half of all ransomware assaults in January (chart beneath). The UK and Australia skilled higher-than-usual assault volumes; CL0P’s current marketing campaign was a think about each of these will increase.
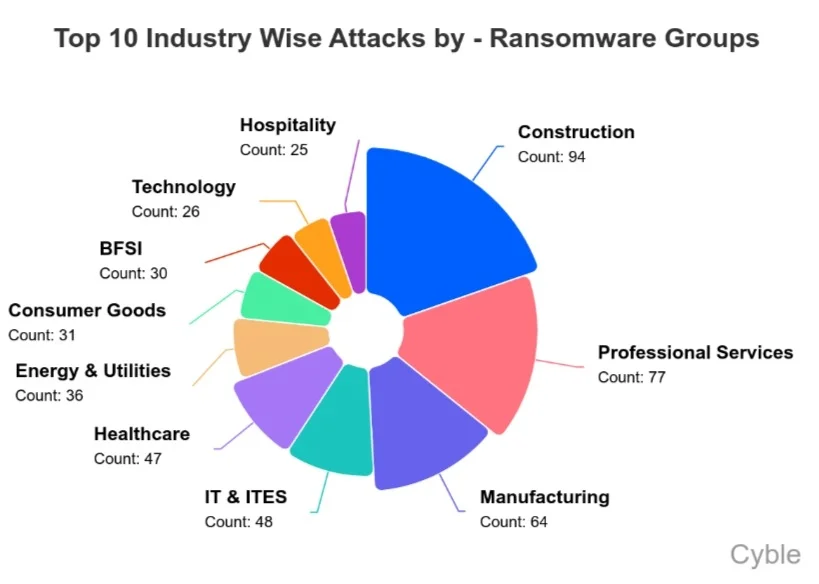
Development, skilled providers, and manufacturing proceed to guide the sectors hit by ransomware assaults, possible on account of opportunistic menace actors concentrating on weak environments (chart beneath). The IT business additionally stays a frequent goal of ransomware teams, possible as a result of wealthy goal the sector represents and the potential to pivot into downstream buyer environments.
Current Ransomware Assaults
Listed here are a few of the most vital ransomware assaults that occurred in January, a number of of which had provide chain implications. Extra particulars shall be offered in Cyble’s forthcoming January 2026 Menace Panorama Report, which shall be printed within the Analysis Reviews part.
As CL0P tends to say victims in clusters, reminiscent of its exploitation of Oracle E-Enterprise Suite flaws that helped drive provide chain assaults to data in October, new campaigns by the group are noteworthy. Among the many claimed victims within the newest marketing campaign have been 11 Australia-based firms spanning a broad vary of sectors reminiscent of IT and IT providers, banking and monetary providers (BFSI), building, hospitality, skilled providers, and healthcare.
Different claimed victims have included a U.S.-based IT providers and staffing firm, a international lodge firm, a main media agency, a UK cost processing firm, and a Canada-based mining firm engaged in platinum group metals manufacturing.
The Everest ransomware group claimed duty for breaching a significant U.S. producer of telecommunications networking gear and claimed to have exfiltrated 11 GB of knowledge. Everest claims the info consists of PDF paperwork containing delicate engineering supplies, reminiscent of electrical schematics, block diagrams, and repair subsystem documentation.
Extra directories reportedly include .brd information, that are printed circuit board (PCB) format information detailing info crucial to {hardware} manufacturing and replication. The group additionally shared a number of samples displaying inside directories, engineering blueprints, and 3D design-related supplies.
The Qilin ransomware group claimed duty for breaching a U.S.-based airport authority liable for managing industrial aviation operations and associated providers. The group shared 16 knowledge samples as proof-of-compromise. The supplies counsel entry to monetary paperwork, telehealth-related studies, inside e mail correspondence, scanned identification paperwork, non-disclosure agreements (NDAs), and different confidential agreements, suggesting publicity of delicate administrative and operational info.
The Sinobi ransomware group claimed a breach of an India-based IT providers firm offering digital transformation, cloud, ERP, and managed providers. The menace group alleges the theft of greater than 150 GB of knowledge, together with contracts, monetary data, and buyer knowledge. Samples shared by the attackers point out entry to inside infrastructure, together with Microsoft Hyper-V servers, a number of digital machines, backups, and storage volumes.
The Rhysida ransomware group claimed duty for breaching a U.S. firm offering life sciences and biotechnology instrumentation and options. In keeping with the menace group, the allegedly stolen knowledge has already been bought, although no info was offered concerning the customer or the worth at which the dataset was marketed.
The sufferer was listed as instantly bought somewhat than positioned beneath a conventional negotiation or countdown mannequin. Regardless of this, samples stay accessible and point out publicity of e mail correspondence, engineering blueprints, undertaking documentation, and non-disclosure agreements (NDAs), suggesting compromise of each technical and company info.
The RansomHouse extortion group claimed duty for breaching a China-based electronics manufacturing firm offering precision parts and meeting providers for international expertise and automotive producers. As proof, RansomHouse printed documentation indicating entry to intensive proprietary engineering and production-related knowledge. The shared supplies reference confidential 3D CAD fashions (STEP/PRT), 2D CAD drawings (DWG/DXF), engineering documentation, printed circuit board (PCB) design knowledge, Gerber information, electrical and format structure knowledge, and manufacturing drawings. Notably, the group claims the compromised archives include knowledge related to a number of main expertise and automotive firms.
INC Ransom claimed duty for breaching a Hong Kong–based mostly producer supplying precision parts to the worldwide electronics and automotive industries. In keeping with the group, roughly 200 GB of knowledge was allegedly exfiltrated. The claimed dataset reportedly consists of client-related info related to greater than a dozen main international manufacturers, plus confidential contracts and undertaking documentation for not less than three main IT firms.
The Qilin ransomware group claimed duty for breaching a Taiwan-based firm working within the semiconductor and electronics manufacturing sector. In keeping with the group, roughly 275 GB of knowledge was allegedly exfiltrated. Based mostly on the file tree info shared by Qilin, the dataset reportedly consists of 19,822 directories and 177,551 information, suggesting broad entry to inside techniques.
The Nitrogen ransomware group leaked greater than 71 GB of knowledge allegedly stolen from a U.S. firm offering engineered parts and techniques for the automotive business. In keeping with the menace group, the uncovered knowledge consists of delicate company and technical info reminiscent of CAD drawings, accounts payable and receivable data, invoices, and steadiness sheet documentation. To substantiate its claims, Nitrogen printed chosen undertaking blueprints and shared a file tree indicating the alleged theft of roughly 116,180 information, suggesting broad entry to inside engineering and monetary techniques.
The Anubis ransomware group claimed duty for breaching an Italian authorities authority liable for the administration, regulation, and improvement of regional maritime port operations. In keeping with the group, the compromised knowledge consists of incident and security studies, logistics and operational knowledge, port infrastructure layouts, audit outcomes, inside studies, and enterprise correspondence.
New Ransomware Teams
Amongst new ransomware teams which have emerged lately, Inexperienced Blood has launched an onion-based knowledge leak web site. Whereas the group has not but publicly named particular victims, it claims that affected organizations are situated in India, Senegal, and Colombia. The group supplies TOX ID and email-based communication channels for sufferer contact. Notably, malware samples related to Inexperienced Blood have been noticed within the wild. The ransomware encrypts information utilizing the “.tgbg” extension and drops a ransom observe titled “!!!READ_ME_TO_RECOVER_FILES!!!.txt”
A brand new ransomware-as-a-service (RaaS) operation named DataKeeper has surfaced, selling an up to date affiliate mannequin known as CrystalPartnership RaaS. The group claims this strategy improves belief by splitting ransom funds instantly between the operator’s and affiliate’s Bitcoin addresses on the time of cost, eradicating reliance on centralized payout dealing with. DataKeeper is marketed as a Home windows-focused ransomware toolkit. The operation claims to make use of a hybrid encryption scheme combining symmetric file encryption with RSA-4096 key safety, distinctive per-build identifiers, and TOR-based cost hyperlinks. Encryption and decryption workflows are tied to a victim-specific ID, with decryption requiring supply of a key file following cost.
The group emphasizes operational options reminiscent of in-memory execution, multithreaded encryption, optionally available shadow copy elimination, community share concentrating on, and evading safety controls.
The menace actor (TA) MonoLock introduced a brand new RaaS operation on the RAMP cybercrime discussion board (the discussion board has since been seized by the FBI). MonoLock’s core design is predicated on Beacon Object Recordsdata (BoF), enabling full in-memory execution, diminished payload publicity, and centralized management from a single post-exploitation command-and-control (C2) occasion with out dropping information.
Whereas BoF utilization is frequent in Home windows environments, MonoLock launched a customized Linux ELF-based BoF loader, derived from the TrustedSec ELFLoader, including chained execution, command packing, encryption, and in-memory deployment. The group promotes a “Zero Panel” extortion mannequin, explicitly rejecting leak websites and Tor-based negotiation panels.
MonoLock claims that avoiding public extortion infrastructure reduces legislation enforcement publicity and leverages silence as negotiation strain, minimizing reputational harm for victims. Associates are recruited beneath a 20% income share with a USD $500 registration charge, alongside a restricted referral program operating from January 11 to March 31.
Conclusion
The persistently excessive degree of ransomware assaults – and the emergence of recent ransomware teams desirous to compete on options and value – spotlight the pressing want for safety groups to undertake a defense-in-depth cyber technique. Cybersecurity greatest practices that may assist construct resilience in opposition to assaults embrace:
- Defending web-facing belongings.
- Segmenting networks and important belongings.
- Hardening endpoints and infrastructure.
- Robust entry controls, permitting no extra entry than is required, with frequent verification.
- A powerful supply of consumer identification and authentication, together with multi-factor authentication and biometrics, in addition to machine authentication with gadget compliance and well being checks.
- Encryption of knowledge at relaxation and in transit.
- Ransomware-resistant backups which are immutable, air-gapped, and remoted as a lot as attainable.
- Honeypots that lure attackers to faux belongings for early breach detection.
- Correct configuration of APIs and cloud service connections.
- Monitoring for uncommon and anomalous exercise with SIEM, Energetic Listing monitoring, endpoint safety, and knowledge loss prevention (DLP) instruments.
- Routinely assessing and confirming controls by means of audits, vulnerability scanning, and penetration assessments.
Cyble’s complete assault floor administration options may help by scanning community and cloud belongings for exposures and prioritizing fixes, along with monitoring for leaked credentials and different early warning indicators of main cyberattacks.
Moreover, Cyble’s third-party threat intelligence can assist organizations rigorously vet companions and suppliers, offering an early warning of potential dangers.


