Safety researchers have demonstrated a non-invasive technique to bypass Microsoft BitLocker encryption on Home windows gadgets in simply 5 minutes with out bodily modifying the {hardware}.
The Bitpixie vulnerability (CVE-2023-21563) permits attackers with temporary bodily entry to extract BitLocker encryption keys, doubtlessly compromising delicate information on company and shopper gadgets that lack pre-boot authentication.
The Bitpixie vulnerability, initially found in 2022 and highlighted on the Chaos Communication Congress (38C3) by safety researcher Thomas Lambertz, exploits a essential flaw in Home windows BitLocker encryption.
In contrast to conventional hardware-based TPM sniffing assaults that require soldering abilities and specialised data, Bitpixie allows software-only exploitation that leaves no bodily hint.
“The exploitation of the abused Bitpixie vulnerability is non-invasive, doesn’t require any everlasting machine modifications and no full disk picture, thereby permitting a quick (~5 minutes) compromise,” explains researcher Marc Tanner from Compass Safety.
This vulnerability particularly targets methods utilizing BitLocker with out pre-boot authentication, which is the default configuration on many Home windows gadgets.
Linux-Based mostly and Home windows PE Exploits
Safety researchers have developed two distinct exploitation strategies, every with totally different necessities and capabilities.
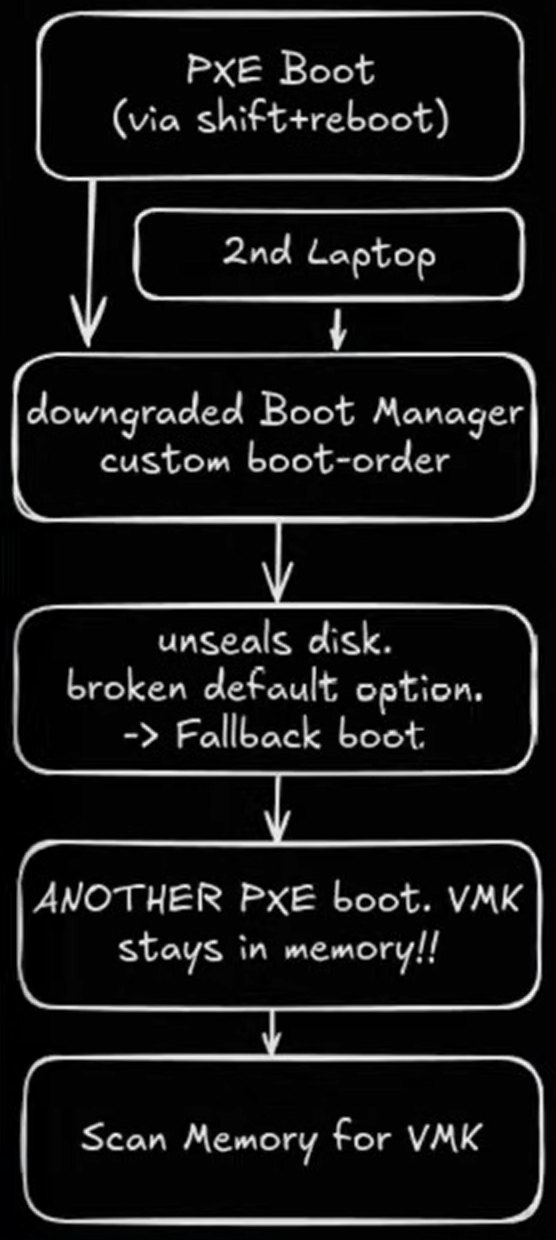
The Linux-based assault follows a multi-step course of that begins by getting into Home windows Restoration Setting and utilizing community boot (PXE) to load a weak Home windows Boot Supervisor.
This downgraded bootloader can then be manipulated to extract the BitLocker Quantity Grasp Key (VMK) from system reminiscence, successfully decrypting the whole drive.
For methods that block third-party signed elements, similar to Lenovo secured-core PCs, researchers created a Home windows PE-based assault that depends solely on Microsoft-signed elements.
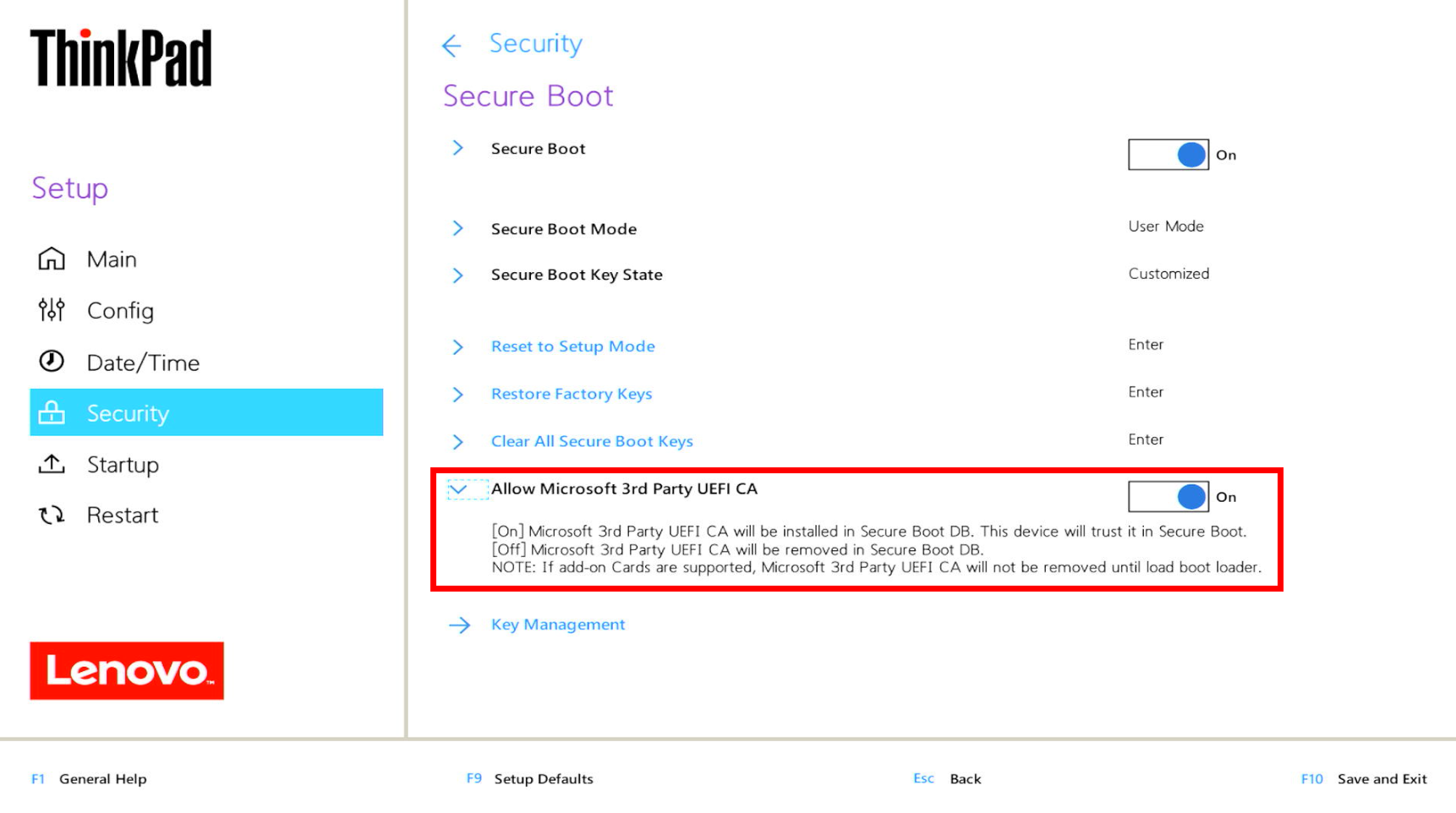
This different technique “makes use of solely core elements signed by Microsoft” and “ought to due to this fact be relevant to all affected gadgets, so long as they belief the Microsoft Home windows Manufacturing PCA 2011 certificates,” in line with safety researchers.
Each strategies require solely non permanent bodily entry, a community connection, and no specialised {hardware}.
Defending Towards BitLocker Bypass Assaults
The elemental flaw in BitLocker’s default configuration stems from its reliance on TPM-only safety with out extra authentication components.
“The vulnerability persists on account of limitations in UEFI certificates storage, with new Safe Boot certificates not anticipated earlier than 2026,” safety researchers notice.
Microsoft has tried to patch the difficulty, however on account of architectural constraints and backward compatibility necessities, the vulnerability stays exploitable by bootloader downgrade strategies.
Organizations can mitigate the chance by implementing pre-boot authentication, forcing customers to enter a PIN or use a USB key earlier than the system boots.
Microsoft safety replace KB5025885 additionally helps cut back publicity by introducing extra Safe Boot certificates and revoking older ones.
Different really useful protections embody disabling community boot through BIOS/UEFI settings and implementing customized BitLocker PINs.
“The Bitpixie vulnerability – and extra typically each {hardware} and software-based assaults – could be mitigated by forcing pre-boot authentication,” concludes the safety analysis crew, emphasizing that the default BitLocker configuration with out this extra layer stays weak.
Discover this Information Attention-grabbing! Comply with us on Google Information, LinkedIn, & X to Get On the spot Updates!

