CharlieKirk Grabber is a Python-based Home windows infostealer that focuses on speedy “smash‑and‑seize” credential theft and knowledge exfiltration somewhat than long-term system management or damaging habits.
It targets browser‑saved passwords, Wi‑Fi keys, Discord tokens, and gaming periods, then exfiltrates the collected knowledge through third‑celebration file internet hosting and encrypted Discord or Telegram channels.
| File Identify | CharlieKirk.exe |
| File Measurement | 19.58 MB |
| File Kind | Executables |
| Signed | Not Signed |
| MD5 Hash | 598adf7491ff46f6b88d83841609b5cc |
| SHA 256 | f56afcdfd07386ecc127aa237c1a045332e4cc5822a9bcc77994d8882f074dd1 |
| First seen wild | Feb 2026 |
Executed underneath the logged‑in consumer context, the binary instantly initializes setting variables, prepares a working listing, and launches a number of knowledge assortment threads to attenuate execution time and consumer visibility.
This multithreaded mannequin mirrors different fashionable Python stealers that emphasize velocity and automation for big‑scale credential harvesting.
On startup, CharlieKirk Grabber profiles the host utilizing native instructions corresponding to SYSTEMINFO and WHOAMI, capturing username, hostname, {hardware} UUID, OS particulars, and community configuration, after which queries an exterior IP info service to acquire the general public IP, ISP, location, and time zone.
In line with the report, the malware operates as a smash-and-grab risk, specializing in rapid knowledge theft somewhat than persistence or long-term system management.
All profiling output is written into native recordsdata inside a brief listing, laying the groundwork for later consolidation and exfiltration.
CharlieKirk Grabber Malware
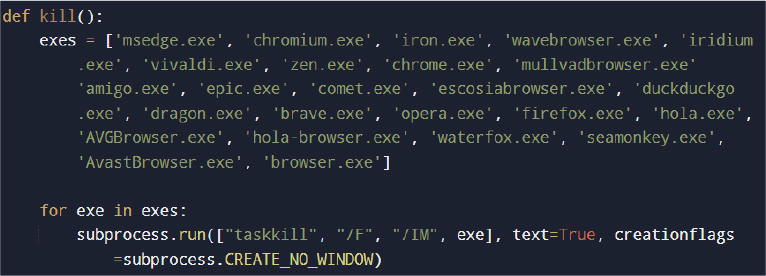
To entry locked browser databases, the malware forcibly terminates energetic browser processes utilizing TASKKILL and different Home windows utilities, suppressing seen home windows with CREATE_NO_WINDOW to stay unobtrusive.
The malware makes an attempt to ascertain persistence by copying its executable to a specified listing and making a scheduled job configured to execute at consumer logon.
It then enumerates a number of Chromium‑primarily based browsers, extracts the grasp key from every Native State file, and makes use of AES‑GCM decryption to get well saved logins, cookies, autofill knowledge, and historical past from SQLite databases corresponding to Login Information, Cookies, Internet Information, and Historical past.
Firefox and different Gecko‑primarily based browsers are focused through NSS, the place encrypted entries in logins.json are decrypted utilizing PK11SDR_Decrypt to reveal saved passwords and associated knowledge.
Past browser shops, CharlieKirk Grabber abuses NETSH to checklist Wi‑Fi profiles and parse the Key Content material subject in cleartext, enabling theft of wi-fi community passwords.
It hunts for Discord authentication tokens throughout commonplace storage paths, decrypts them utilizing the identical Chromium grasp key method, and validates tokens in opposition to Discord APIs to extract account metadata corresponding to username, electronic mail, cellphone, MFA standing, and Nitro subscription particulars.
The malware additionally targets gaming ecosystems by gathering Minecraft session recordsdata and Steam session knowledge, enabling account hijacking even with out password reuse. Lastly, it captures a desktop screenshot utilizing Python imaging libraries and provides this to the staged knowledge set.
Mitigations
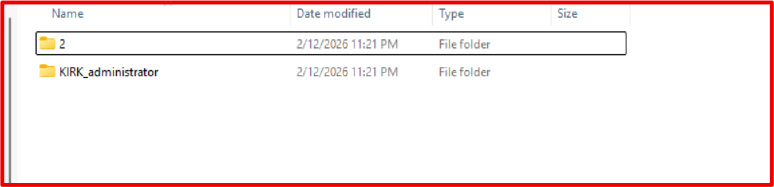
All harvested artifacts are staged underneath a brief listing (for instance KIRK_administrator underneath %LOCALAPPDATApercentTemp), then compressed right into a single ZIP archive for environment friendly switch.
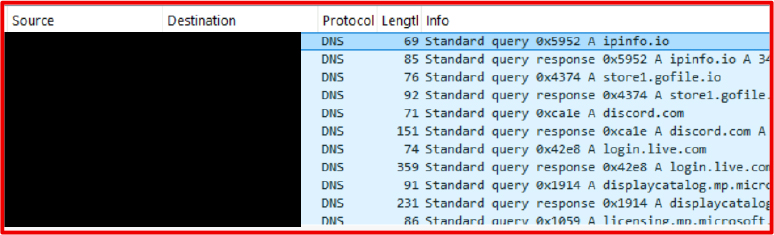
The archive is uploaded to a file‑internet hosting service corresponding to GoFile, which returns a public obtain hyperlink continuously abused by commodity stealers for log trafficking.
That hyperlink is then despatched to attacker‑managed infrastructure through Discord webhooks or Telegram bots over HTTPS, leveraging trusted platforms and encrypted channels to mix with professional visitors.
After profitable exfiltration, the malware deletes the momentary listing and archive, decreasing forensic artifacts and aligning with “gather‑and‑pack” patterns seen throughout infostealer households.
CharlieKirk Grabber makes use of a number of protection‑evasion methods however no subtle anti‑evaluation capabilities.
It makes an attempt UAC elevation utilizing IsUserAnAdmin(), and when operating with administrative rights, it invokes PowerShell so as to add Microsoft Defender exclusions through Add‑MpPreference, decreasing the possibility of on‑entry detection.
It additionally creates a scheduled job through schtasks /sc onlogon to take care of persistence when configured, although its main design stays quick knowledge theft somewhat than lengthy‑time period footholds.
Behaviorally, it depends closely on LOLBins (TASKKILL, NETSH, SYSTEMINFO, CMD, POWERSHELL) for discovery and credential entry, mapping to ATT&CK methods corresponding to T1082 System Info Discovery, T1555.003 Credentials from Internet Browsers, T1560 Archive Collected Information, T1562.001 Impair Defenses, and T1567.002 Exfiltration to Cloud Storage.
Defenders ought to monitor for irregular patterns of compelled browser course of termination adopted by intensive entry to browser SQLite recordsdata and speedy ZIP archive creation inside %TEMP% or %LOCALAPPDATA%.
Community monitoring ought to concentrate on uncommon HTTPS connections to Discord webhooks, Telegram Bot APIs, and file‑sharing companies like GoFile, particularly in environments the place such companies are usually not enterprise essential.
Strategic controls embody implementing MFA, limiting browser password storage, blocking unsanctioned file‑internet hosting platforms, and adopting Zero Belief rules to scale back the blast radius of stolen credentials.
On the endpoint degree, organizations ought to allow EDR detections for netsh wlan present profile key=clear, suspicious PowerShell execution modifying Defender preferences, and execution of unsigned binaries from consumer‑writable paths corresponding to %TEMP%, %APPDATA%, and %LOCALAPPDATA%.
Observe us on Google Information, LinkedIn, and X to Get Immediate Updates and Set GBH as a Most well-liked Supply in Google.

