A brand new GlassWorm-linked provide chain assault abusing the Open VSX Registry, this time through a suspected compromise of a reputable writer’s credentials moderately than typosquatted packages.
The Open VSX safety crew assessed the exercise as according to leaked tokens or different unauthorized entry to the publishing pipeline, underscoring how stolen developer credentials could be weaponized to push malicious updates by way of trusted channels.
On January 30, 2026, 4 long-standing Open VSX extensions maintained beneath the “oorzc” namespace acquired malicious updates embedding the GlassWorm malware loader.
These extensions FTP/SFTP/SSH Sync Instrument (v0.5.1), I18n Instruments (v1.6.8), vscode mindmap (v1.0.61), and scss to css (v1.3.4) had beforehand operated as reputable utilities for greater than two years and collectively amassed over 22,000 downloads on Open VSX previous to the poisoned releases.
Whereas Open VSX reveals rounded “Okay” values in its UI, Socket’s evaluation of the underlying counts confirms the mixed whole exceeds 22,000 downloads, highlighting the potential publicity amongst builders.
oorzc namespace with 4 printed extensions (Supply : Socket).The assault chain hinges on a staged loader launched within the newest malicious variations throughout all 4 extensions.
Malicious VSX Packages Found
Every .vsix file incorporates an almost an identical loader in extension.js that makes use of AES-256-CBC to decrypt an embedded hex-encoded blob after which instantly executes the decrypted content material with eval at runtime.
This design hides the true payload from static inspection, with the crucial logic solely materializing in reminiscence.
Stage 1 of this decrypted payload performs setting checks to keep away from infecting Russian-language and Russia-adjacent methods, utilizing locale, time zone, and UTC offset indicators as crude geofencing.
Methods that match Russian indicators are skipped solely, reflecting typical prison OPSEC issues.
If the host passes these checks, Stage 1 then turns to an uncommon command-and-control mechanism: it resolves its next-stage configuration from Solana blockchain transaction memos.
As a substitute of hardcoding C2 domains, GlassWorm makes use of on-chain memos as a dynamic “useless drop,” permitting the attacker to rotate infrastructure with out republishing the extension.
As soon as the C2 pointer is obtained, the loader focuses its execution path on macOS methods, explicitly checking for Darwin earlier than triggering Stage 2.
That subsequent stage, applied as a Node.js JavaScript implant, is tailor-made for information theft and persistence on macOS developer endpoints.
Stage 2 creates a working listing beneath /tmp/ijewf, aggregates a variety of delicate artifacts, compresses them into /tmp/out.zip, and exfiltrates the archive to hardcoded IP-based endpoints through curl.
The gathering scope is broad: browser cookies, login databases, and type historical past from Chromium-based and Firefox-family browsers, wallet-extension information comparable to MetaMask, desktop cryptocurrency pockets recordsdata (together with Electrum, Exodus, Atomic, Ledger Reside, Trezor Suite, Binance, and TonKeeper), macOS keychain databases, Apple Notes information, Safari cookies, FortiClient VPN configurations, and focused paperwork from Desktop, Paperwork, and Downloads.
Open-Supply Ecosystem Exploited
Critically, the implant additionally harvests developer-related secrets and techniques, together with ~/.aws credentials and config, and ~/.ssh keys, known_hosts, and configuration recordsdata, elevating the danger of cloud account takeover and lateral motion inside enterprise environments.
The payload goes additional by searching for tokens and secrets and techniques utilized in widespread developer workflows. It inspects npm configuration for _authToken values and reveals conduct according to npm token discovery and validation, whereas additionally referencing GitHub authentication artifacts.
Compromised GitHub and npm tokens may permit attackers to hijack non-public repositories, entry CI secrets and techniques, poison builds, or push tampered releases downstream, extending the blast radius effectively past a single workstation.
This newest exercise marks a notable evolution from earlier GlassWorm campaigns first reported in October 2025, which leaned closely on typosquatting and brandjacking of in style extensions.
In distinction, the present incident abuses a longtime writer account with a multi-year historical past and significant adoption indicators.
The identical “oorzc” writer additionally maintains Visible Studio Market listings with hundreds of installs, reinforcing that the actor focused a trusted id moderately than fabricating a brand new one.
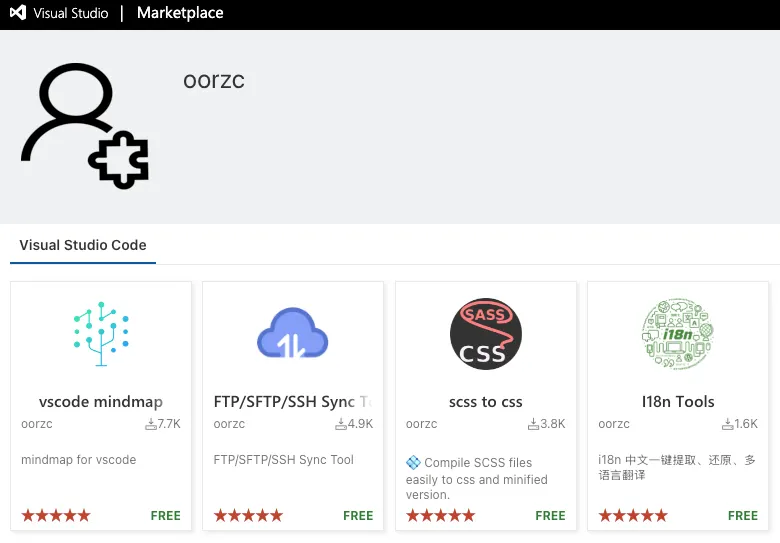
oorzc on Visible Studio Market (Visible Studio Code) itemizing 4 extensions (Supply : Socket).Socket’s findings give attention to the Open VSX ecosystem, and there’s no indication on this report that the Visible Studio Market listings themselves had been compromised.
After Socket’s January 30, 2026 disclosure, the Eclipse Basis / Open VSX Registry safety crew moved shortly.
They eliminated the malicious releases, deactivated two Open VSX tokens related to the writer, and, because of repeated malware hits and quite a few variations, eliminated all variations of oorzc.ssh-tools from the registry and positioned it on the Open VSX malware record, whereas preserving earlier clear variations of the opposite three extensions.
The response illustrates each the velocity and the bounds of registry-side defenses: as soon as developer credentials are stolen, trusted distribution paths could be abused till the compromise is detected and tokens are revoked.
Observe us on Google Information, LinkedIn, and X to Get Prompt Updates and Set GBH as a Most well-liked Supply in Google.

