A vital vulnerability, dubbed “GerriScary,” has been found in Google’s Gerrit code-collaboration platform, placing not less than 18 main Google tasks—together with ChromiumOS, Chromium, Dart, and Bazel—prone to unauthorized code submissions by hackers.
This flaw, uncovered by Tenable Cloud Analysis, highlights the risks of misconfigured permissions in open-source improvement environments and the potential for large-scale provide chain assaults.
The GerriScary Vulnerability
Gerrit, developed by Google, is a extensively used web-based system for code evaluation and collaboration.
It permits builders to suggest, talk about, and approve code modifications earlier than they’re merged into mission repositories.
Nonetheless, Tenable researchers discovered {that a} mixture of default permissions and logic flaws in Gerrit’s evaluation course of may enable any registered consumer to inject malicious code into trusted Google tasks with out detection.
The vulnerability facilities on two foremost Gerrit mechanisms: permissions and labels. Permissions outline what actions customers can carry out, whereas labels (or “Submit Necessities”) are used to gatekeep which code modifications are eligible for merging.
In lots of Google tasks, the default “addPatchSet” permission was granted to all registered customers, permitting them to add new variations of current code modifications—even when they weren’t the unique writer.
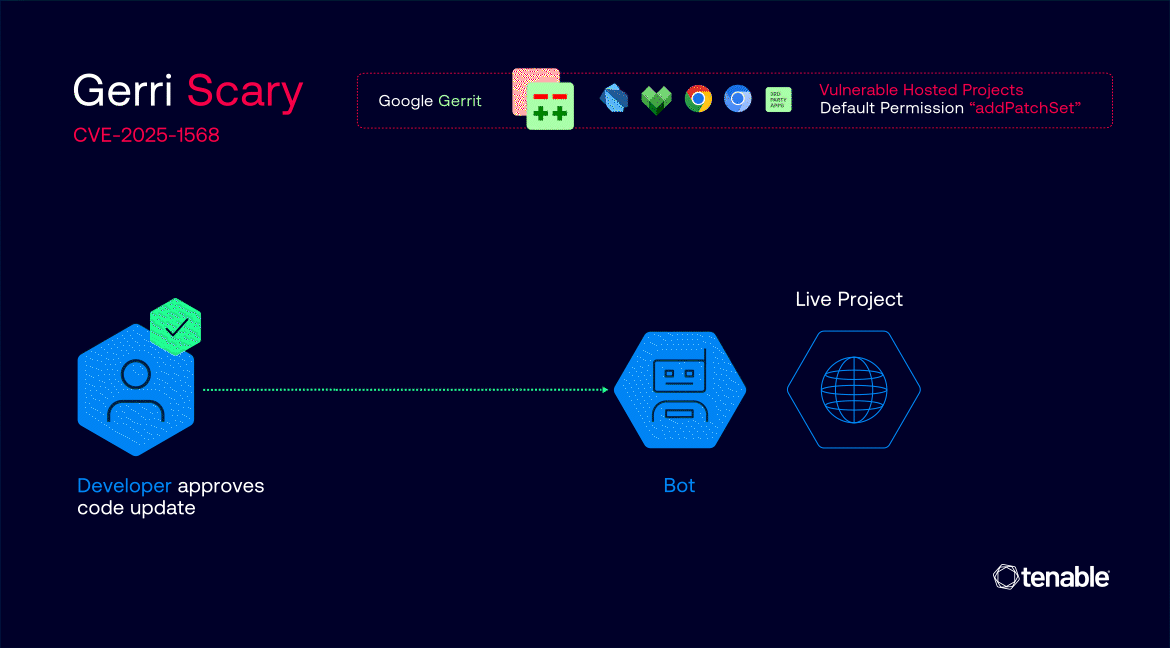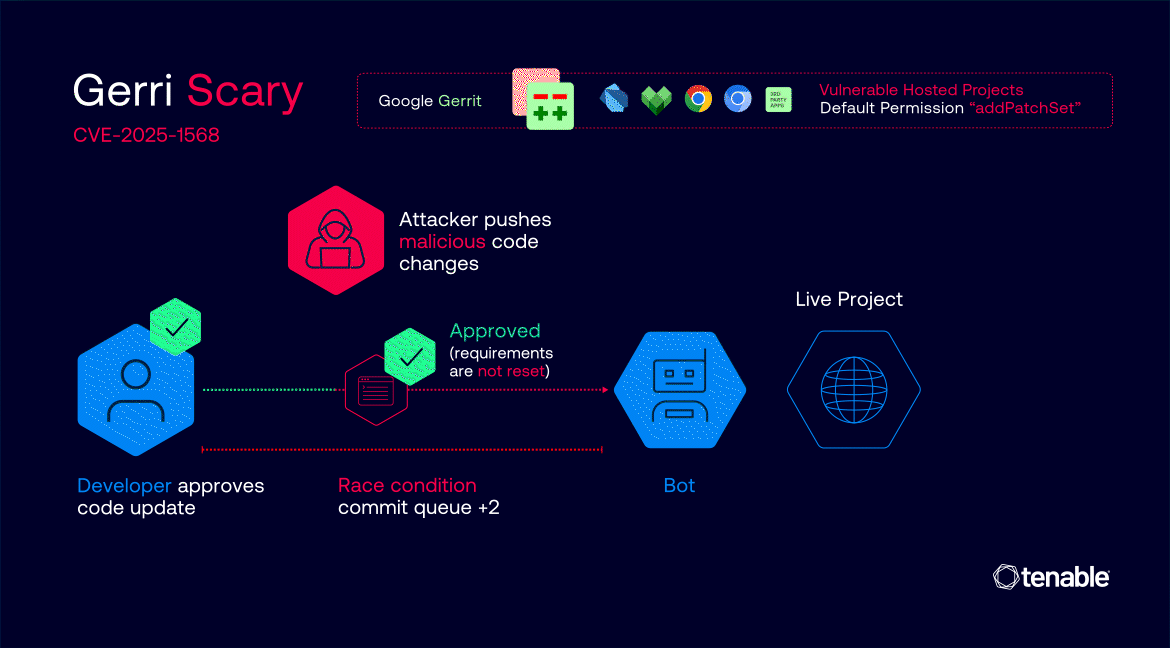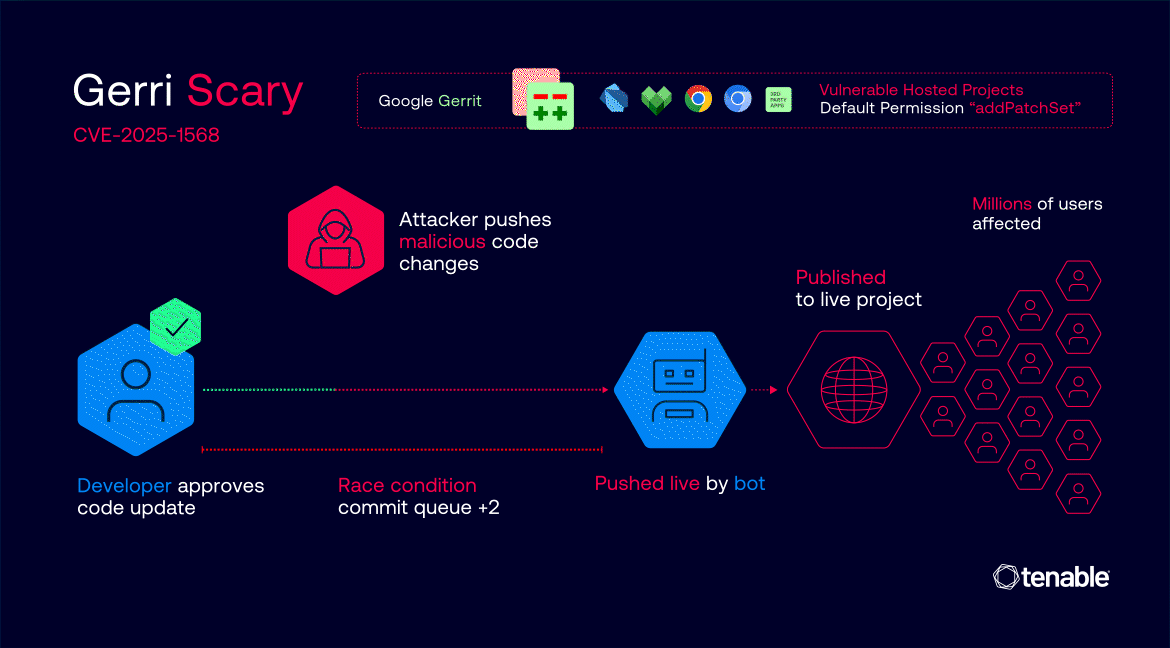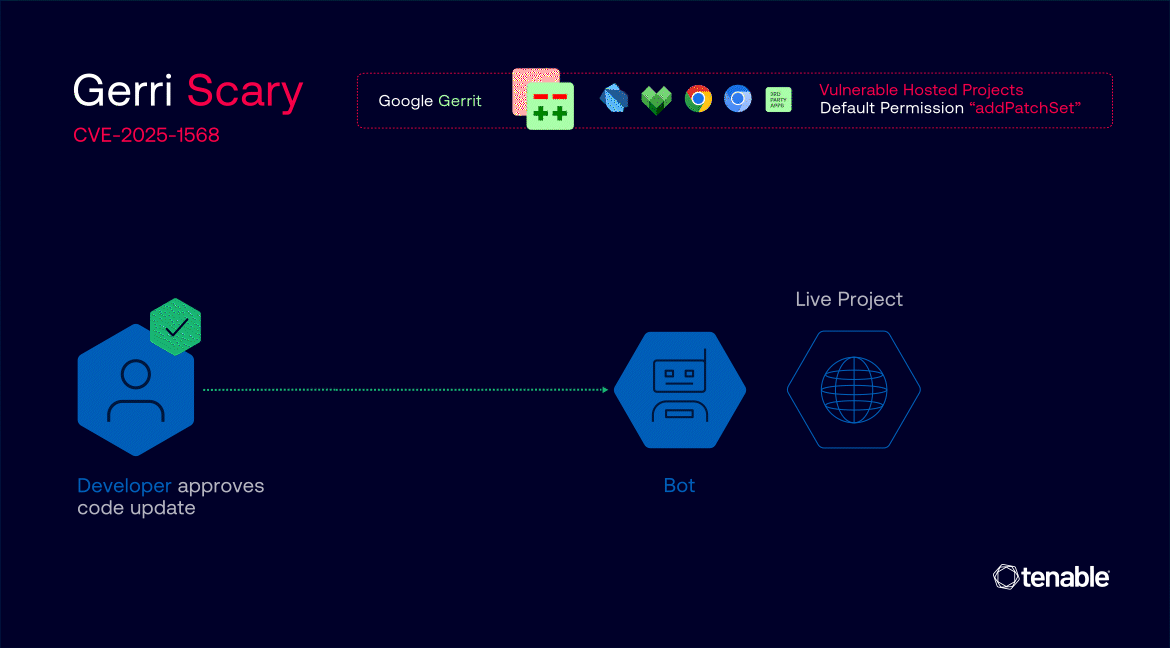
The true hazard emerged from a misconfiguration in the best way Gerrit handles label “Copy Situations.” Within the affected tasks, label approvals—similar to “Code-Evaluate” and Google’s customized “Commit-Queue”—have been set to persist throughout new patch units, even when the underlying code modified.
This meant {that a} code change might be totally authorized and prepared for merging, and an attacker may then inject malicious code as a brand new patch set with out resetting the approval standing.
Attackers may automate the method by monitoring for code modifications that had already acquired all needed approvals, then racing to add a malicious patch set simply earlier than Google’s automated bots merged the develop into the repository.
In some circumstances, this race window was so long as 5 minutes, offering ample alternative for exploitation.
Impacted Initiatives and Fast Actions
The vulnerability affected not less than 18 main Google tasks, together with ChromiumOS (CVE-2025-1568), Chromium, Dart, and Bazel. The vulnerability allowed unauthorized code submission to those tasks earlier than remediation.
| Mission Identify | Description | Notable CVE(s) |
| ChromiumOS | Open-source OS powering ChromeOS units | CVE-2025-1568 |
| Chromium | Open-source browser mission (foundation for Chrome) | |
| Dart | Programming language for shopper improvement | |
| Bazel | Construct and check device for giant codebases | |
| Third-party Chromium packages | Neighborhood-maintained Chromium elements | |
| … | (Extra tasks as per Appendix A) |

Whereas Google has since remediated the flaw in its personal tasks by tightening permissions and correcting label copy circumstances, the danger stays for third-party organizations that use Gerrit and haven’t reviewed their configurations.
Safety specialists warn that any group utilizing Gerrit ought to instantly audit their permissions, particularly the “addPatchSet” setting, and evaluation their label copy circumstances to make sure that approvals will not be improperly retained throughout code modifications.
The GerriScary incident underscores the significance of rigorous entry management and configuration administration in open-source improvement.
Trade leaders like Google can fall sufferer to delicate misconfigurations that open the door to stylish provide chain assaults. As software program provide chains grow to be extra complicated, the necessity for sturdy safety practices and steady monitoring is extra urgent than ever.
Organizations are urged to be taught from Google’s expertise and proactively safeguard their very own improvement pipelines towards related vulnerabilities.
Discover this Information Fascinating! Observe us on Google Information, LinkedIn, and X to Get Instantaneous Updates

