A dependable VMware atmosphere reporting device, RVTools, was momentarily infiltrated earlier this week on Might 13, 2025, to disseminate the sneaky Bumblebee loader virus, serving as a sobering reminder of the vulnerabilities current in software program provide chains.
This incident, detected by a safety operations group by way of a high-confidence alert from Microsoft Defender for Endpoint, revealed a classy assault vector the place a seemingly professional installer turned a conduit for malicious payloads.
An worker making an attempt to put in RVTools triggered the alert as Defender flagged a suspicious file, model.dll, executing from the installer’s directory-a habits extremely atypical for this broadly trusted utility used throughout enterprises for VMware atmosphere evaluation.
This breach underscores the rising menace of provide chain assaults, the place even established instruments might be weaponized by adversaries to infiltrate safe methods.
Provide Chain Assault Targets Trusted VMware Utility
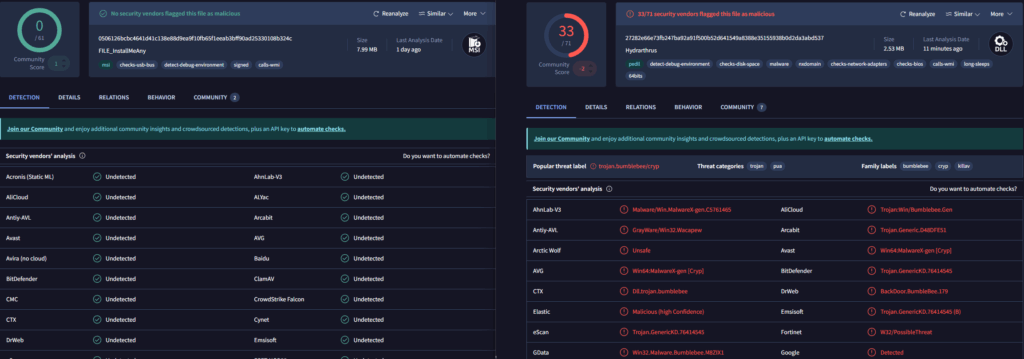
Upon deeper investigation, the compromised RVTools installer was discovered to include a file considerably bigger than its professional counterpart, with a mismatched hash in comparison with the clear model listed on the official web site.

Evaluation through VirusTotal confirmed the severity, with 33 out of 71 antivirus engines figuring out the file as a customized variant of the Bumblebee loader-a malware household infamous for facilitating preliminary entry in cyber campaigns, typically paving the way in which for ransomware or post-exploitation frameworks like Cobalt Strike.
The file’s metadata additional raised crimson flags, that includes weird and intentionally obfuscated entries comparable to “Hydrarthrus” as the unique filename and surreal descriptors like “elephanta ungroupable clyfaker gutturalness” underneath product particulars.
In keeping with ZeroDay Labs Report, these cryptic phrases, presumably hinting at symbolic or mythological references, served as a distraction from the file’s malicious intent.
Inside an hour of submission to VirusTotal, public detections surged from 4 to 16, coinciding with the RVTools web site quickly going offline earlier than returning with a corrected, smaller file matching the official hash-strong proof of a fleeting but focused compromise of the distribution channel.
Technical Evaluation Reveals Malicious Intent
The fast response suggests the maintainers acted swiftly to interchange the contaminated installer, however not earlier than exposing an unknown variety of customers to the menace.
The incident highlights the essential want for strong file integrity checks and safe distribution mechanisms, as attackers exploited the belief in RVTools to deploy malware able to devastating downstream results on Home windows methods.
In response, the affected system underwent a full Defender scan, with the malicious file quarantined and no indicators of lateral motion detected.
The safety group verified older RVTools installations throughout the community, cross-referenced obtain histories with recognized clear hashes, and shared inner indicators of compromise (IOCs) with menace intelligence models whereas notifying the software program maintainer.
This breach serves as a potent lesson within the significance of validating file integrity by way of hash verification, scrutinizing metadata for anomalies, and leveraging platforms like VirusTotal to gauge menace publicity.
It additionally requires distributors to implement stringent safety practices, together with code signing and HTTPS-only downloads, to safeguard in opposition to such hijacks.
Organizations that just lately downloaded RVTools are urged to confirm installer hashes and monitor for executions of model.dll from consumer directories.
Indicators of Compromise (IOCs)
| Indicator | Particulars |
|---|---|
| File Title | model.dll |
| Malware Variant | Bumblebee Loader |
| Suspicious Metadata | Authentic File Title: Hydrarthrus |
| Detection Supply | VirusTotal (33/71 AV engines) |
Discover this Information Attention-grabbing! Observe us on Google Information, LinkedIn, & X to Get Prompt Updates!

