In a significant discovery, cybersecurity researchers at Kaspersky Securelist have discovered a brand new espionage exercise concentrating on authorities workplaces throughout Southeast and East Asia. The marketing campaign, which probably started in February 2025, makes use of a rootkit to cover deep inside a pc’s core, making it invisible to straightforward safety instruments.
Kaspersky hyperlinks the assault to a bunch referred to as HoneyMyte (aka Bronze President or Mustang Panda). In keeping with their evaluation, the hackers are particularly concentrating on Myanmar and Thailand utilizing a malicious driver file named ProjectConfiguration.sys.
Bypassing the Digital Guard
As we all know it, most antivirus applications scan for suspicious recordsdata on the floor. Nonetheless, they fail to establish this assault as a result of the driving force registers as a mini-filter, a software that sits deep within the system’s site visitors management.
To look reputable, the hackers used a stolen digital certificates from Guangzhou Kingteller Know-how (Serial: 08 01 CC 11 EB 4D 1D 33 1E 3D 54 0C 55 A4 9F 7F), which, though expired in 2015 however nonetheless helps the malware bypass inside warnings.
To additional disguise its tracks, the driving force makes use of dynamic decision, a method that scrambles its inside code so safety software program can’t simply perceive what it’s doing. Additional probing revealed the driving force is extremely cussed. If an antivirus tries to delete or rename it, the driving force merely blocks the motion. It even “blinds” Microsoft Defender by tampering with its “altitude” settings. This mainly permits the malware to sit down “under” the antivirus within the system, intercepting instructions earlier than the safety software program even sees them, the weblog submit explains.
The ToneShell Backdoor
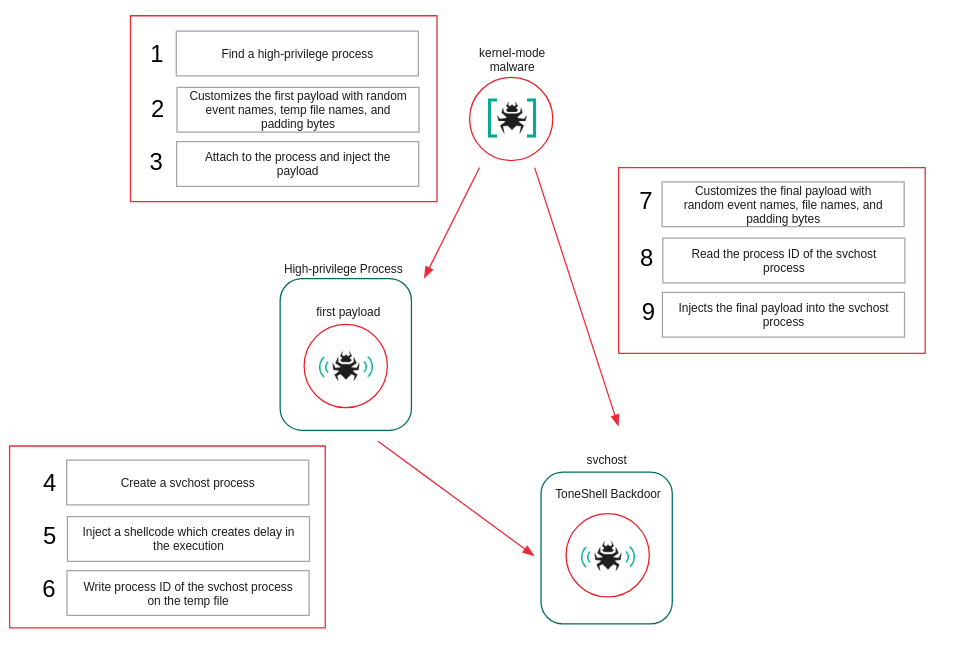
The final word purpose of this intrusion is to drop a spy software referred to as the ToneShell backdoor, which acts as a secret gateway for hackers to steal recordsdata, obtain information, or run distant instructions.
A noteworthy discovering is that the group registered their management servers (avocadomechanism.com and potherbreference.com) by way of NameCheap again in September 2024, months earlier than the precise assaults started.
“That is the primary time we’ve seen ToneShell delivered via a kernel-mode loader,” researchers famous, explaining that it provides the spy software a excessive degree of safety from being caught.
In the course of the assault, the driving force delivers two payloads: first, it creates a “host” course of (svchost) to behave as a decoy, after which it injects the ToneShell backdoor into that course of. To maintain their communication secret, ToneShell makes use of a Faux TLS trick, mimicking the markers of safe TLS 1.3 site visitors.
Apparently, most victims have been already contaminated with older HoneyMyte instruments just like the ToneDisk USB worm or PlugX. As a result of the malware runs totally within the pc’s reminiscence and makes use of shellcodes to guard its personal processes, it is vitally arduous to detect. Due to this fact, Kaspersky researchers advocate deep reminiscence audits and cautious monitoring of community site visitors to catch these pretend connections.