Nitrogen, a ransomware pressure, has emerged as a serious menace to organizations worldwide, with a specific deal with the monetary sector. First recognized in September 2024, Nitrogen has quickly gained notoriety for its refined assault strategies and devastating influence.
This ransomware encrypts crucial knowledge and calls for substantial funds for decryption. It has focused industries reminiscent of finance, development, manufacturing, and expertise, primarily in america, Canada, and the UK.
Cybersecurity specialists warn that Nitrogen’s superior techniques and evolving methods pose a extreme danger to organizations unprepared for its precision and persistence. The usage of malware evaluation and menace intelligence instruments can mitigate these dangers and forestall incidents.
Nitrogen’s Options and Techniques
Nitrogen’s complicated assault chain begins with malvertising campaigns on engines like google like Google and Bing. The adverts trick customers into downloading trojanized installers disguised as legit software program, reminiscent of AnyDesk, WinSCP, or Cisco AnyConnect.
As soon as put in, the ransomware makes use of instruments like Cobalt Strike and Meterpreter shells to determine persistence, transfer laterally inside networks, and execute its payload. Nitrogen modifies registry keys and schedules duties to make sure they continue to be energetic even after the system reboots. It conducts thorough system reconnaissance, identifies high-value targets inside networks to maximise the influence, and employs superior evasion strategies.
Amongst Nitrogen’s most notable victims are:
- SRP Federal Credit score Union (USA): in December 2024 this assault launched Nitrogen to the broader world and uncovered the monetary sector’s vulnerability.
- Crimson Barrels (Canada): the online game developer had 1.8 terabytes of delicate knowledge extorted, together with sport supply codes and inner paperwork.
- Management Panels USA: a customized management panel options supplier was listed as a sufferer on Nitrogen’s darkish internet leak website in September 2024, indicating a profitable breach and potential knowledge exfiltration.
- Kilgore Industries: In December 2024 the manufacturing firm confronted a ransomware assault attributed to the Nitrogen group.
Gathering Risk Intelligence on Nitrogen
Not a lot is but identified about Nitrogen modus operandi resulting from restricted public knowledge. The primary publicly out there supply of data is the report by StreamScan. It presents key indicators of compromise and a few insights into the strategies however is gentle on particulars. That is the place ANY.RUN’s specialists step in, providing deeper insights via dynamic evaluation and menace intelligence enrichment.
The StreamScan report particulars a couple of crucial IOCs:
- Ransomware File: A malicious executable with the
SHA-256 hash 55f3725ebe01ea19ca14ab14d747a6975f9a6064ca71345219a14c47c18c88be
- Mutex: A novel identifier,
nvxkjcv7yxctvgsdfjhv6esdvsx, created by the ransomware earlier than encryption.
- Weak Driver:
truesight.sys, a legit however exploitable driver used to disable antivirus and endpoint detection instruments.
- System Manipulation: Use of bcdedit.exe to disable Home windows Secure Boot, hindering system restoration.
These indicators may be researched through Risk Intelligence Lookup to search out extra IOCs, behavioural knowledge, and technical particulars on Nitrogen assaults.
1. Monitoring the Mutex
Nitrogen creates a singular mutex to make sure just one occasion of the ransomware runs at a time. Utilizing the mutex’s identify as a TI Lookup search request, one can uncover over 20 associated malware samples analyzed by the customers of ANY.RUN’s Interactive Sandbox.
syncObjectName:”nvxkjcv7yxctvgsdfjhv6esdvsx”
For every pattern, an evaluation session may be explored to complement the understanding of the menace and collect extra indicators not featured in public analysis. These IOCs can be utilized for tuning monitoring, detection and response programs to make sure proactive safety towards the malware.
2. Exposing the Weak Driver
Nitrogen exploits truesight.sys, a legit driver from RogueKiller AntiRootkit, to kill AV/EDR processes and thus disable antivirus and endpoint detection instruments. This driver is utilized by menace actors as a result of it’s not inherently malicious, so it doesn’t set off customary defences. ANY.RUN’s TI Lookup reveals over 50 analyses linked to truesight.sys:
sha256:"Bfc2ef3b404294fe2fa05a8b71c7f786b58519175b7202a69fe30f45e607ff1c"
By parsing these analyses, groups see how the motive force may be abused, from terminating safety processes to evading detection. Looking by the motive force’s identify with the “CommandLine” parameter ends in a choice of system occasions involving the motive force:
Discovering such exercise induces safety groups to well timed block the vulnerabilities of such varieties.
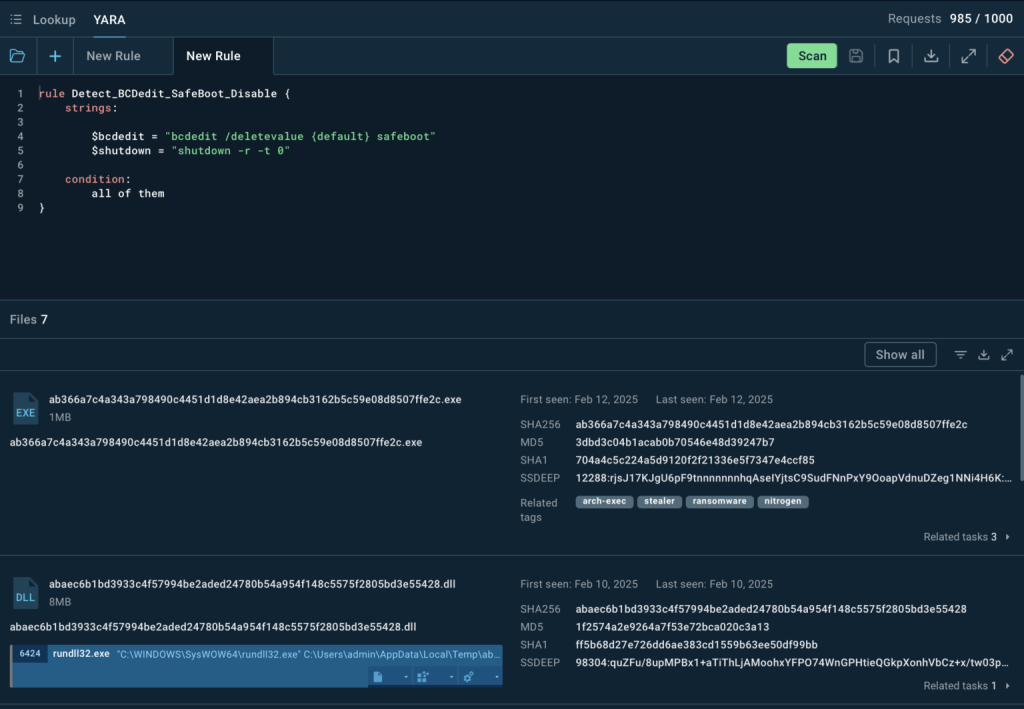
3. Catching System Manipulation
Nitrogen makes use of the Home windows utility bcdedit.exe to disable Secure Boot, a restoration mechanism that helps restore an contaminated system. ANY.RUN permits analysts to make use of YARA guidelines to seek for this behaviour, figuring out malware that tampers with system settings.
A YARA search in TI Lookup returns a number of information linked to this tactic, every with an related evaluation session that reveals extra IOCs.
By integrating these IOCs into SIEM or EDR programs, organizations can detect and block makes an attempt to switch Home windows boot settings earlier than encryption begins, stopping Nitrogen in its tracks.
To defend towards threats like Nitrogen, safety groups ought to:
- Block identified malicious infrastructure and domains.
- Monitor for uncommon use of PowerShell, WMI, and DLL sideloading.
- Educate workers about phishing and social engineering techniques.
- Use menace intelligence companies to proactively hunt for associated IOCs and TTPs.
- Use DMARC, DKIM, and SPF to forestall e-mail spoofing, a tactic typically used to ship Nitrogen’s malicious payloads.
- Frequently replace software program and apply patches to shut vulnerabilities exploited by Nitrogen.
Strengthen Your Defenses with ANY.RUN
Within the face of rising threats like Nitrogen ransomware, real-time evaluation and menace intelligence are now not non-obligatory, they’re important. To mark its ninth anniversary, ANY.RUN is launching a limited-time promotion to assist safety professionals keep forward of recent cyber threats with the Interactive Sandbox and Risk Intelligence Lookup options.
Seize the present: further Sandbox licenses on your workforce, or double TI Lookup quota.
Disclosure: This text was offered by ANY.RUN. The data and evaluation introduced are based mostly on their analysis and findings.