A Russian-speaking menace actor attributed to the username “koneko” has resurfaced with a complicated new botnet named Tsundere, found by Kaspersky GReAT round mid-2025.
This marks a big evolution from a earlier provide chain marketing campaign that focused Node.js builders in October 2024, revealing disturbing parallels in methodology and infrastructure.
Utilizing typosquatting strategies registering bundle names almost an identical to reputable libraries the attacker distributed 287 malicious Node.js packages by npm.
The October 2024 marketing campaign demonstrated the menace actor’s preliminary proof-of-concept for compromising the JavaScript ecosystem.
Fashionable targets included Puppeteer, Bignum.js, and varied cryptocurrency packages, affecting Home windows, Linux, and macOS customers throughout the developer group.
The unpackaging script is accountable for recreating this construction, together with the node_modules listing with all its libraries, which incorporates packages crucial for the malware to run.
The marketing campaign was short-lived, deserted after detection, nevertheless it offered essential perception into the attacker’s capabilities.
New Botnet, Expanded Scope
Tsundere represents a matured model of this menace. Slightly than relying solely on provide chain compromise, the botnet employs a number of an infection vectors together with MSI installers disguised as well-liked video games (Valorant, CS2, R6X) and PowerShell scripts.
Preliminary discovery of 1 implant traced again to a Distant Monitoring and Administration (RMM) instrument that downloaded a suspicious PDF.msi file, demonstrating the menace actor’s willingness to take advantage of reputable instruments for malware distribution.
The MSI installer technique proved remarkably efficient, bundling Node.js executables with malicious JavaScript information that run within the background.
The installer executes by Home windows Installer CustomAction desk, spawning hidden Node.js processes that load encrypted bot scripts utilizing AES-256-CBC encryption.
The PowerShell variant equally downloads Node.js from official repositories, making a facade of legitimacy whereas deploying an identical performance.
What distinguishes Tsundere is its use of Ethereum good contracts for command-and-control infrastructure resilience.
Slightly than counting on conventional domains weak to takedown, the botnet shops WebSocket C2 addresses on the Ethereum blockchain utilizing pockets 0x73625B6cdFECC81A4899D221C732E1f73e504a32 and contract 0xa1b40044EBc2794f207D45143Bd82a1B86156c6b.
This strategy permits operators to rotate C2 servers at will with out DNS-level interruption.
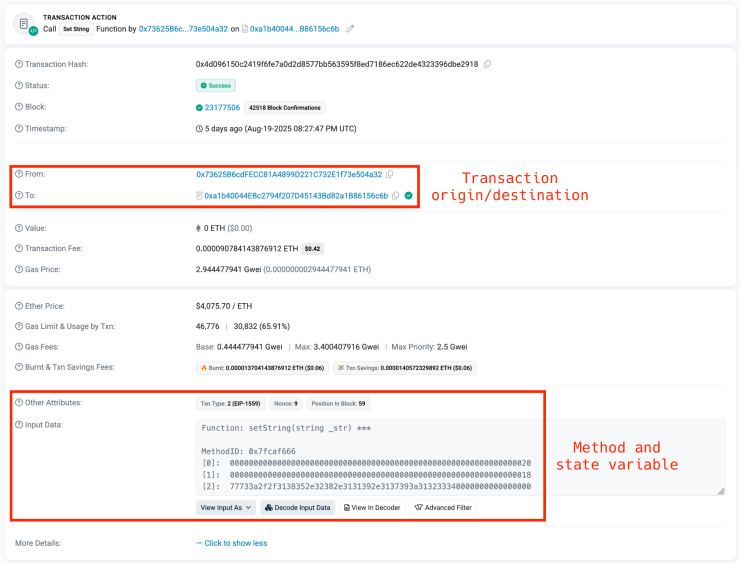
Contaminated machines question public Ethereum RPC endpoints to retrieve the present C2 handle, establishing encrypted WebSocket connections for command execution.
The botnet employs dynamic JavaScript code analysis, enabling operators to deploy arbitrary performance by the C2 panel.
Market Mannequin and Infrastructure
The Tsundere management panel options an open-registration system permitting any consumer to construct customized bots, create malware variants, and supply companies on an built-in market.
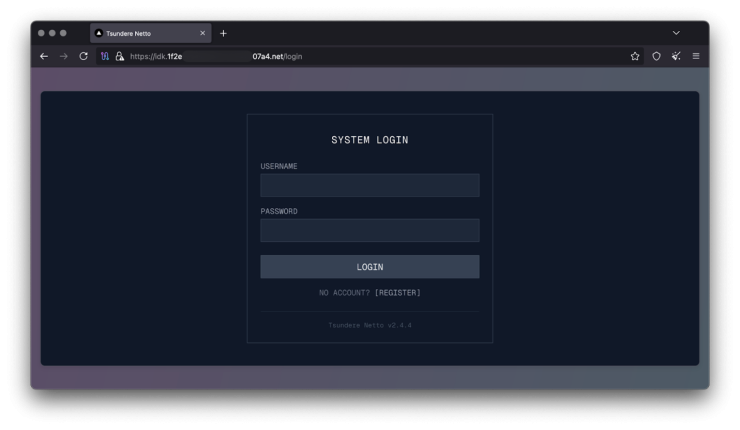
The panel integrates Monero pockets performance, SOCKS proxy capabilities, and a Construct system for producing distinctive bot variants. On the time of study, 90-115 bots maintained energetic connections.
Attribution proof hyperlinks Tsundere to the 123 Stealer (a industrial stealer out there for $120 month-to-month) by shared infrastructure, with each threats working from the identical backend servers.
The menace actor’s profile on darkish net boards listed the title “node malware senior,” reinforcing experience in Node.js-based malware growth.
With Tsundere infrastructure actively responding to bot connections and the underlying menace actor concurrently selling extra malware, safety researchers anticipate this menace to escalate relatively than diminish.
Organizations ought to monitor for associated threats and implement strong provide chain safety practices to mitigate the chance posed by this evolving botnet household.
Observe us on Google Information, LinkedIn, and X to Get Instantaneous Updates and Set GBH as a Most well-liked Supply in Google.

