A Ukrainian nationwide has pleaded responsible in federal court docket in Brooklyn to conspiracy to commit laptop fraud in reference to the deployment of the Nefilim ransomware in opposition to company laptop networks in america and different nations.
Artem Aleksandrovych Stryzhak, 35, of Barcelona, Spain, admitted that he conspired with others to make use of the ransomware to break sufferer techniques and extort funds from firms focused within the marketing campaign.
Prosecutors say Stryzhak was given entry to the Nefilim ransomware code in June 2021 by the directors of the ransomware in trade for 20% of any proceeds generated from ransom calls for.
Utilizing his account on the web Nefilim “panel,” he and co‑conspirators researched potential victims, together with by pulling info on firm measurement, income, and phone particulars from public on-line databases earlier than launching assaults.
Like another ransomware marketing campaign, the Nefilim assault additionally concerned producing a novel ransomware executable for every sufferer, together with a corresponding decryption key and tailor-made ransom word. If a sufferer selected to pay the ransom, the conspirators offered the decryption key to revive the encrypted recordsdata.
As a part of their extortion ways, the group threatened victims with the publication of stolen knowledge on publicly accessible “Company Leaks” websites until calls for have been met.
Stryzhak was arrested in Spain in June 2024 and extradited to america in April 2025. In accordance with the US DoJ’s press launch, he’s scheduled for sentencing in Could 2026 and faces a statutory most of 10 years in jail, although a federal decide will decide his precise time period primarily based on U.S. sentencing pointers and different components.
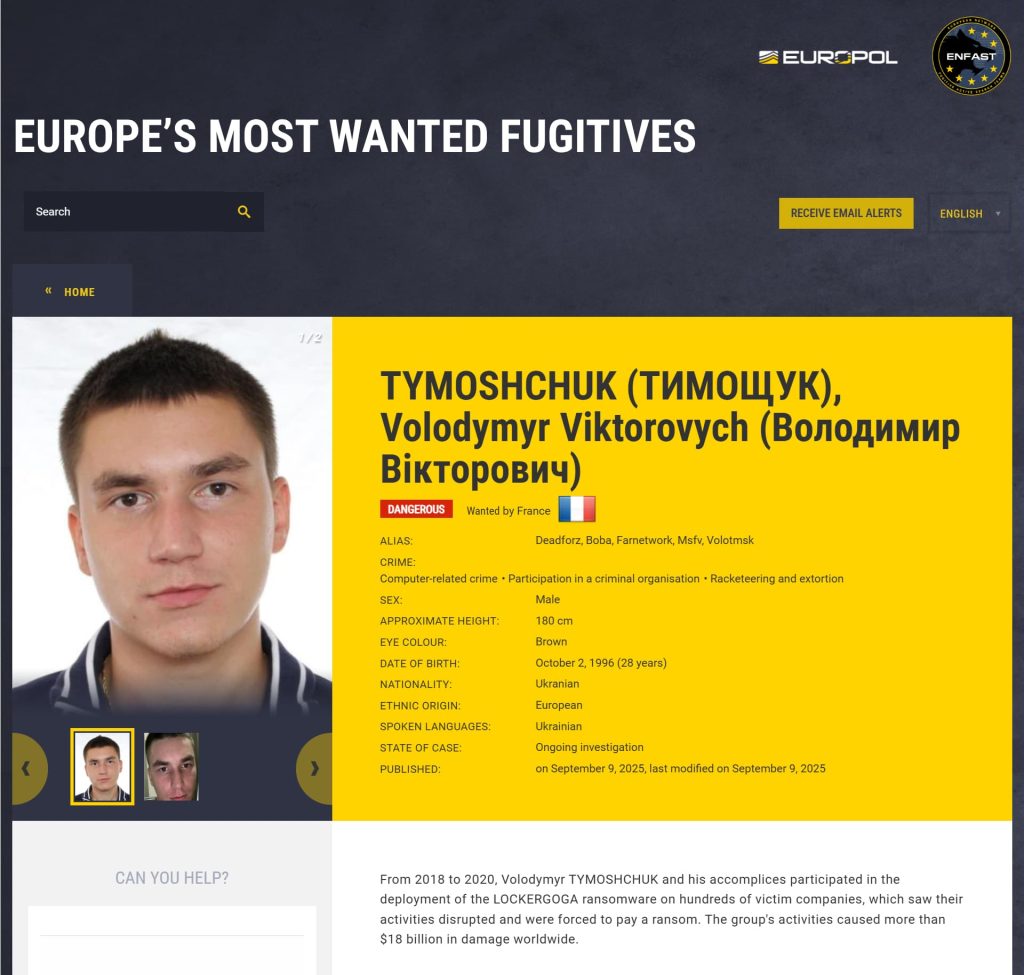
The US Division of State’s Transnational Organised Crime Rewards Program has provided as much as $11 million for info resulting in the arrest or conviction of Stryzhak’s alleged co‑conspirator, Volodymyr Tymoshchuk, who stays at massive. Tymoshchuk has additionally been linked to different strains like LockerGoga and MegaCortex.
Historical past and Standing of Nefilim Ransomware
First noticed in 2020, Nefilim is believed to be a successor to the Nemty ransomware household. It gained traction via its double-extortion method, exfiltrating delicate knowledge and threatening public leaks by way of its “Company Leaks” website until ransom calls for have been met.
In accordance with SentinelOne’s evaluation, all through its lively interval, Nefilim targets have included excessive‑income firms and huge enterprises, particularly in america, Canada, Australia, and Europe.
Though Nefilim exercise has dropped since 2022, its ways, particularly the mixture of knowledge theft and encryption, have influenced many ransomware campaigns that adopted.
Though Nefilim isn’t as lively immediately and elements of its operation have been taken down by regulation enforcement, its strategies nonetheless affect how ransomware teams function. Using double extortion and affiliate-based assaults has change into a typical observe for most of the newer campaigns.